Minecraft skins on the Play Store discovered as malware
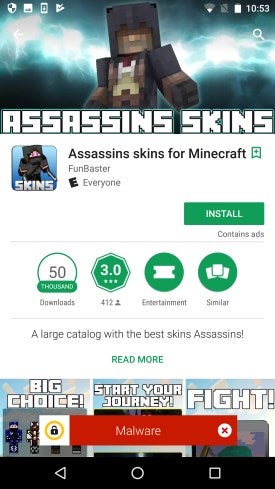
At the surface, those apps would provide an actual in-game use (the provided example, shown to the right, is an assassin character skin). Upon install, however, the apps would connect to a command-and-control server and would start sending ad requests. While no ads were actually displayed, this still resulted in ad revenue for the developer and battery loss for the user.
Furthermore, the apps later added the infected devices to a botnet — in essence, this is a large group of devices which unwittingly perform commands given by the owner of the botnet. The most common use is to DDoS (distributed denial of service) websites, which means to shower them with so many fraudulent requests their servers stop responding to actual users.
Symantec dubbed the malware "Sockbot," and says it has identified eight apps with a total of more than 2 million installs. All of those came from a single developer, called "FunBlaster." Google has already been notified of the problem and has since taken them down.
Granted, none of this is out of the ordinary, but there is one detail that makes this a particularly nasty type of attack: Minecraft's target demographic. While the data is scarce, most sources claim the majority of the game's user base is no older than 15 years. Combine this with the basic functionality of the app being strictly cosmetic (and thus unlikely to excite many adults), and it seems clear that the developer's strategy was to primarily target children.
Follow us on Google News











Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: