Exploit found on iOS 13 allows hacker to see your contacts even when your iPhone is locked
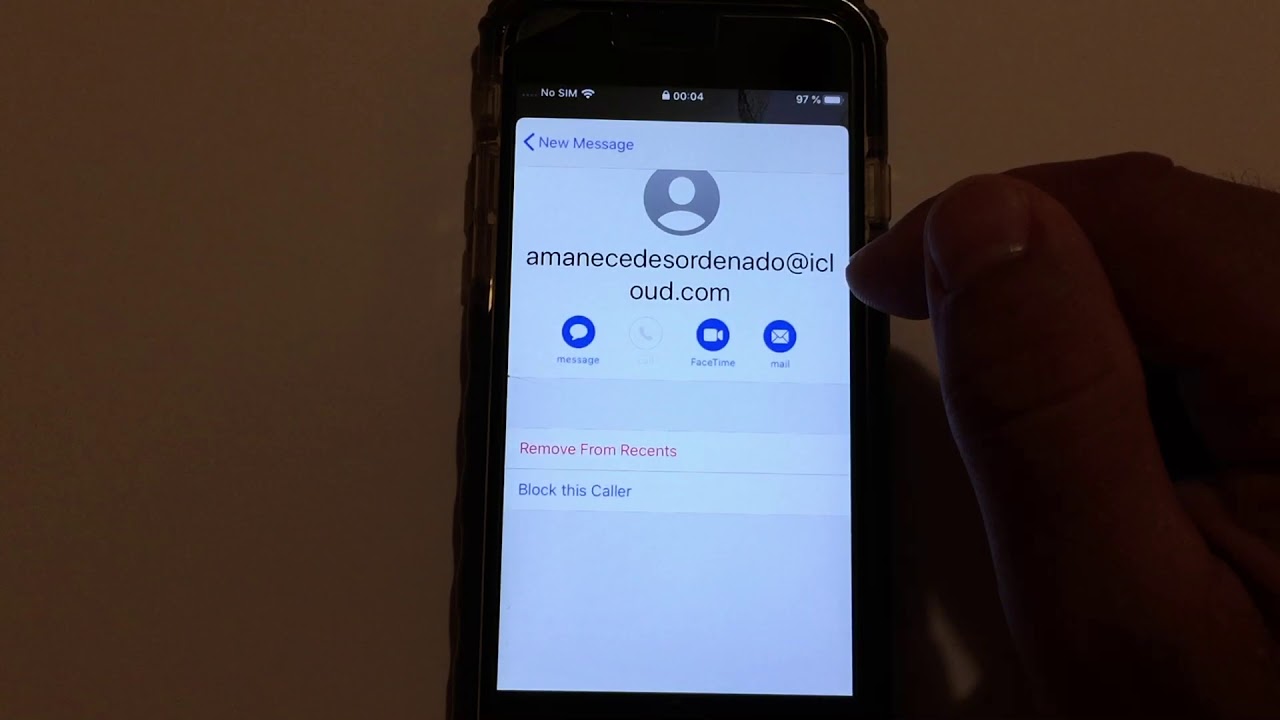
Even though iOS 13 won't be released until September 19th, a security researcher named Jose Rodriguez has already posted a YouTube video (via The Verge) showing off an exploit he discovered on the next major build of Apple's mobile operating system. By making a FaceTime call and then enabling the Siri VoiceOver feature, an iPhone user can gain access to a phone owner's contacts list. That can provide the hacker with a list of phone numbers, email addresses, street addresses and more all without unlocking the device. The phone owner's photos are still protected. VoiceOver allows Siri to read the text that appears on an iPhone's display and is considered an accessibility feature for those who are blind or suffer from impaired vision.
Like the exploit he discovered last year, the new iOS 13 vulnerability requires that the hacker get a hold of the target's iPhone long enough to complete the entire process. It also requires a second phone to initiate the FaceTime call with the target iPhone. Apple is expected to have this exploit patched in iOS 13.1, which should be rolled out starting on September 30th.
The video that Rodriguez sent to Apple can be found below.


Follow us on Google News











Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: