An increasingly paranoid guide to smartphone security

Is it no exaggeration at all to say that your smartphone is your life? Your messages, your bank account, maybe even your smart-home hub: all accessible through that handset. With all the data we entrust to our phones, and all the private information we send through them, smartphone security is of the utmost importance. But are you doing everything you can to keep your phone and its data safe?
Will you follow these measures through to the extreme, ending up living in a signal-blocking Faraday cage and mumbling to yourself about a Snapchat-driven conspiracy to rig the 2016 election? We can get you there, but baby steps first: let's take a look at some of the more reasonable security precautions you can take to help keep your phone safe and your data private.
Locking the front door

Especially with the rise in availability, performance, and accuracy of fingerprint scanners on phones lately, implementing a secure lockscreen is trivial and the most basic step you can take towards securing your phone.
Encryption
Once you've got that lock in place, your next step is putting it to good use. Beyond preventing nosy co-workers from snooping through your photos when you turn your back on your phone, modern lockscreens do double-duty by also serving as our access points to full-disk phone encryption. This is exactly the sort of security that's at the heart of the recent FBI San Bernardino iPhone 5c hack, designed to prevent even advanced threats that have physical access to your phone (and its on-board storage) from being able to read your data.

On Android, the situation is a little more hit-and-miss. Newer phones running Marshmallow are supposed to have encryption enabled by default, but older or less powerful handsets might not. In that case, you can always flip it on yourself by pulling up phone settings, going to the Security screen, and tapping the “Encrypt phone” option.
Already we're facing a trade-off: storage access speeds are going to be lower with encryption enabled. That performance penalty is less of a big deal on modern phones with processing power to spare (and dedicated hardware encryption engines), but things will never be quite as fast as with no encryption at all.
No one listening on the line
For all the steps you can take to keep the information that's physically on your phone nice and safe, they won't do you much good when you need to start communicating with other people – and sending messages out to their phones. You've got no shortage of messaging options out there, but which are going to keep your conversations safe from anyone who might be listening in?
Secure IM
Right now, the gold standard in secure communications is end-to-end encryption. That means that your phone encrypts its messages before they even leave the handset, and they stay encrypted the whole time they're moving across cellular networks and the internet's backbone, before finally being decrypted on the recipient's device. The important bit here is that the companies offering end-to-end services can't themselves decrypt any in-transit messages.
Signal also supports voice-call encryption
There are plenty of third-party ways to do end-to-end instant message encryption, and easily the most popular is WhatsApp. Last month the service announced that its end-to-end efforts covered users across mobile platforms, and encrypted messages as well as data like photos, voice, and video.
If WhatsApp isn't your thing, you can always turn straight to the horse's mouth: WhatsApp uses technology from Open Whisper Systems to implement its encryption, and OWS has its own secure messaging app, Signal. The app's open-source, so you can always pore over the code and make sure there are no hidden backdoors, and implementations are available for both Android and iOS.
Email privacy
That's got us covered for IM, but what about some old-school email action? Email encryption is the grandfather of encrypted communication services, and if you thought the current debate over smartphone encryption was a novel occurrence, you owe it to yourself to read up on the early-'90s debut of Pretty Good Privacy, an encryption package the government investigated under the same laws that regulate arms trafficking.
At this point, you're quite the little digital-privacy maven. You've got your phone secure, and your communications secure. Time to kick back and enjoy the fruits of your labors? Sure, you could, but you'd be missing out on some of the really fun tin-foil-hat stuff.
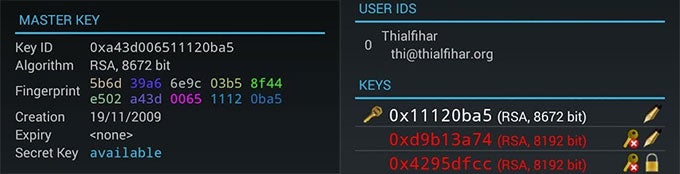
Key management in Android Privacy Guard
Batten down the hatches
End-to-end encryption may keep your messaging private, but what about the rest of your app data? Well-written software will implement its own encryption as it talks back home to its server, but you can take things to the next level with a VPN.
Virtually secure
A virtual private network essentially acts like an encrypted tunnel, protecting every last bit of data that leaves your phone before it even hits a cellular tower. If you're worried the phone company can see what you do on your phone, or you're concerned who's really behind that suspiciously convenient open Wi-Fi access point you've been using, this is a great way to protect all your data in one fell swoop.
Always wear protection
We've spent all this time girding our loins in anticipation of wireless eavesdroppers, but what about wired threats? Oooh, we like the way you're thinking, seeing data-stealing risks everywhere.
Could that innocent-looking charging kiosk be loaded with USB-vectored malware just waiting for the chance to leap over to our phones? There's no way to know, which is exactly what makes this such ideal paranoia fuel.

USB condom: now with gold-plated connectors, for your phone's pleasure.
Now, Android's already taken some steps to prevent against rogue USB cables messing with our phones when we just want a charge, as Marshmallow defaults new USB connections to charge-only mode. Such software protections are great, but nothing beats a good hardware fix, and we find ours in the form of a USB “condom.”
Go open-source or go home

Replicant seeks to remove not just Google software, but any and all non-open code from Android. That creates some big problems for compatibility, as drivers for key phone hardware are often provided as binary blobs that can't be adequately vetted for security - so Replicant does without them. Running Replicant means using some very old phone hardware (we're talking Galaxy S2, first-gen Galaxy Note, or Galaxy Nexus era) and losing key features like Wi-Fi and Bluetooth in the process (thank god cellular data still works). But if you want to make sure that your smartphone OS itself isn't spying on you, this is the path you should be prepared to take.

Your personal data: GIVE IT TO US
They're all out to get me
Do you hear that? Are those helicopters? They always fly low to the horizon, so you don't know they're coming until they're right on top of you. What? Smartphones? You stay away from my phone, you hear?
The perfect-ish algorithm
You're still relying on the public-key encryption schemes of OpenPGP, iMessage, or WhatsApp? You fool. Don't you know that they're based on nothing more secure than math? Why, the second quantum computing becomes viable (and who's to say it hasn't yet for a certain three-letter-agency whose initials rhyme with MFJ?), they're as good as useless.

Your phone's encrypted storage similarly won't be much good once those quantum supercomputers start factoring prime numbers as easily as they add 2+2, so how are we to keep our data safe? Once again, it's physical security to the rescue.
Removed from the equation
If your most valuable data isn't on your phone at all, it suddenly becomes a lot harder to get at, so why not bring external storage into the mix? If your phone supports microSD, that's a good start, but it's not without its trade-offs. Those cards can be hard to get to on a lot of phones, preventing quick removal when you need to make that data disappear. And if you're using adoptable storage in Marshmallow, you can't be inserting and removing cards willy-nilly.

Then you just need to keep your important documents, your private photos, and all your most valuable data stored on that flash drive.
Pop it on your phone when you need access, and when the men in black come looking for it, you can always swallow it to conceal the evidence.
On second thought, carrying a drive like that around sounds like an unacceptable risk. What you're going to want to do is dig a nice, deep hole in your backyard, seal that flash drive up tight, and bury it where no one will find it. While we're at it, it's probably safer for you to bury your phone, too. Remember, you didn't read any of this.

references: Open Whisper Systems, Replicant, Zendo (iTunes, Play Store), VyprVPN, OpenVPN, OpenKeychain, Android Privacy Guard
Follow us on Google News












Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: