RCS vulnerabilities can help a hacker take control of your bank account

Rich Communication Service, or RCS, is the next generation in wireless messaging. Unlike SMS/Text, which uses a wireless operator's cellular connection, RCS runs through a carrier's data network. This allows messages to be sent over Wi-Fi when possible. It also will lead to an increase in the number of characters allowed per message to 8,000 from the 160 cap that text has. In addition, RCS issues "read receipts" so that users know when their message has been read by the recipient. And when someone is typing a response to an RCS dispatch, a three-dot indicator will let a user know that an incoming message is being composed. Group messages with up to 100 participants can take place, and larger files containing images and videos can be shared.
The U.S. wireless carriers have big plans for the platform. All four major U.S. carriers have formed the Cross Carrier Messaging Initiative (CCMI) and are planning to deliver an RCS based messaging app next year to their Android toting customers. The wireless operators are planning to monetize RCS by allowing users to purchase tickets, visit their favorite brands, and even buy products without leaving the messaging app. Meanwhile, as it did in the U.K. and France earlier this year when it pulled an end-run around the carriers by releasing an RCS messaging app, Google recently started rolling out RCS Chat to all Android phones in the states. Those receiving it have to select the Android Messages app set as their default messaging platform.
Hackers using vulnerabilities found on RCS can steal one time passwords and make changes to users' online accounts
But there does seem to be a dark side to RCS as discovered by Germany (SRLabs). The security firm says that the process of getting Android handsets ready for RCS leaves the platform wide open to be hacked and that there is very little protection for users. Attackers can take over user accounts, and the most widely used RCS Client at the moment (the aforementioned Android Messages app) does not do enough validation of domains, certificates, and user identity. As a result, hackers can spoof a domain name and even allow caller ID spoofing and fraud.
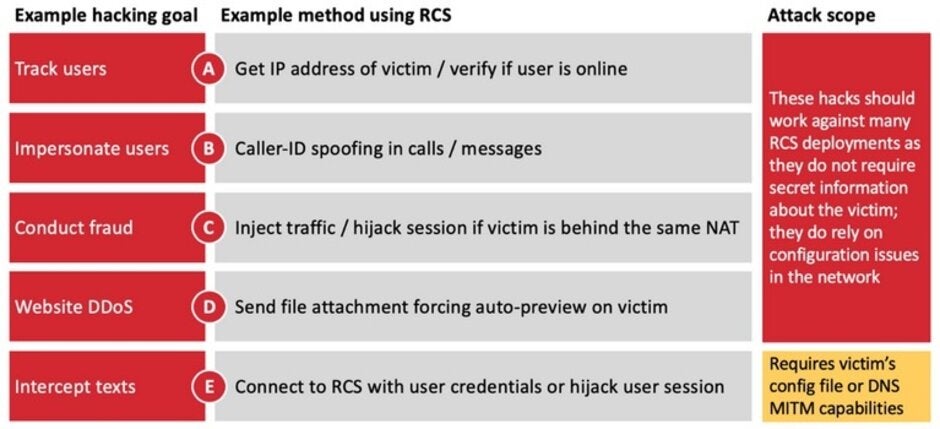
Some of the attacks that hackers can do through the RCS vulnerabilities
SRLabs found that through RCS, hackers can track users and verify if they are online. Spoofing caller ID, the hackers can pretend to be someone else. The vulnerabilities in the platform can allow a bad actor to hijack a one-time password sent by SMS; this could allow an unauthorized bank transaction to be approved, or help transfer the control of an account to a hacker. The report notes that "The underlying issue is that the RCS client, including the official Android messaging app, does not properly validate that the server identity matches the one provided by the network during the provisioning phase. This fact can be abused through DNS spoofing, enabling a hacker to be in the middle of the encrypted connection between mobile and RCS network core."
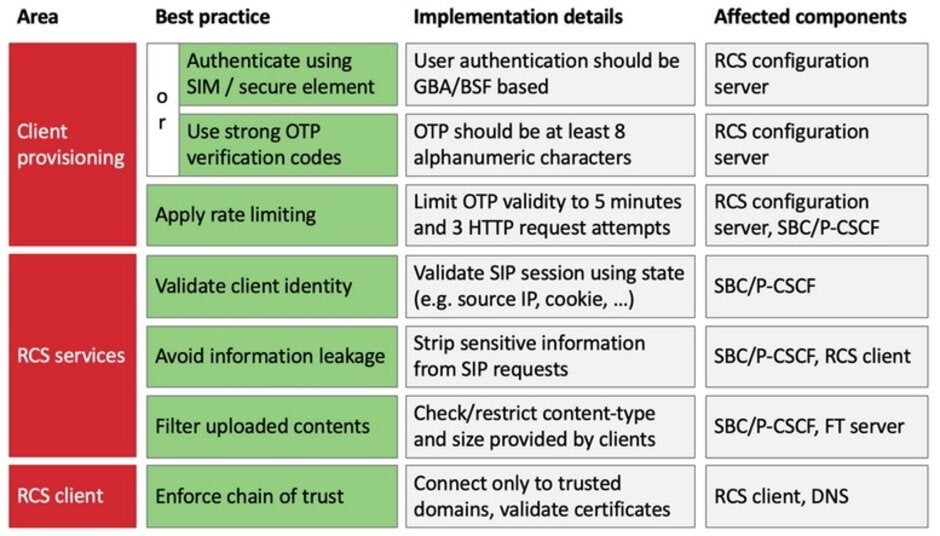
RCS attacks can be mitigated by using these best practices
SRLabs says that the vulnerabilities can be corrected. Some of the suggestions include the use of "strong" one time password codes, and employing information from a user's SIM card to authenticate the user. The RCS client being employed (for example, the Android Messages app) should connect only to trusted domains and validate certificates.
If RCS is going to live up to its potential, the vulnerabilities need to be patched. And that is especially true if the carriers plan on monetizing it. Consumers are going to want to use a messaging app that they can trust and at this point, it isn't clear that RCS can be fully trusted.
Follow us on Google News














Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: