Sophisticated version of ransomware "kidnaps" your data on Android phones

Similar to the idea of paying a ransom to a kidnapper in order to get the kidnapped individual returned alive, ransomware is a type of malware that results in a bad actor demanding payment or else the victim will have his/her personal data published for all to see. Another threat demands a payment or else the victim will be blocked from accessing the data over his/her mobile device. Either way, this is digital extortion.
Ransomware evolves on mobile devices
Last Thursday, October 8th, Microsoft's 365 Defender Research Team wrote a report about the latest evolution of mobile Ransomware. The report stated the Research Team "found a piece of a particularly sophisticated Android ransomware with novel techniques and behavior, exemplifying the rapid evolution of mobile threats that we have also observed on other platforms. The mobile ransomware, detected by Microsoft Defender for Endpoint as AndroidOS/MalLocker.B, is the latest variant of a ransomware family that’s been in the wild for a while but has been evolving non-stop. This ransomware family is known for being hosted on arbitrary websites and circulated on online forums using various social engineering lures, including masquerading as popular apps, cracked games, or video players. The new variant caught our attention because it’s an advanced malware with unmistakable malicious characteristic and behavior and yet manages to evade many available protections, registering a low detection rate against security solutions."
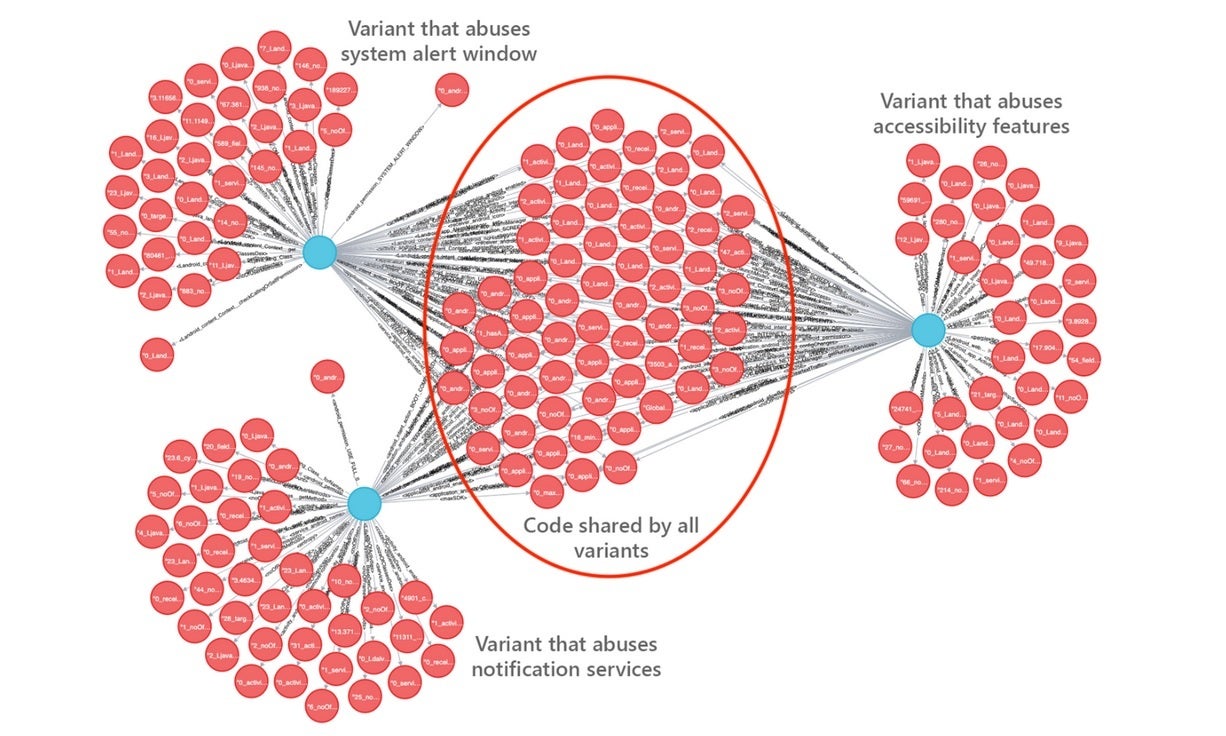
Different variants of ransomware
To disseminate the ransom, the instructions are placed on a note that blocks access to a display. Older versions of ransomware used to rely on a permission called "SYSTEM_ALERT_WINDOW" that draws a window that can't be dismissed. Originally designed for system alerts or errors, the bad actors hijack the permission forcing the hacker-controlled UI to cover the entire screen. Users are thus blocked from having access to their device forcing them to pay the ransom. Google fought back by removing the SYSTEM_ALERT_WINDOW error and alert window. It also elevated the permission status of SYSTEM_ALERT_WINDOW to special permission by putting it into the “above dangerous” category. This means that instead of making just a single click, users have to go through many screens to approve apps that ask for permission.
The hackers "evolved" the malware by using accessibility features, but these are easily detectable. Now, these apps have continued to evolve by using the "Call" notification (which requires users' immediate attention), and the callback method on Android. The combination of these two components triggers the ransom note. And the Microsoft 365 Defender Research Team says that the evolution is far from being over. The report says, "In fact, recent variants contain code forked from an open-source machine learning module used by developers to automatically resize and crop images based on screen size, a valuable function given the variety of Android devices.
The frozen TinyML model is useful for making sure images fit the screen without distortion. In the case of this ransomware, using the model would ensure that its ransom note—typically fake police notice or explicit images supposedly found on the device—would appear less contrived and more believable, increasing the chances of the user paying for the ransom." Another important aspect of the mobile ransomware variant is that it could give hints of what to expect from future malware attacks."
Tanmay Ganacharya, who leads the Microsoft Defender research team, says, "It’s important for all users out there to be aware that ransomware is everywhere, and it’s not just for your laptops but for any device that you use and connect to the internet. The effort that attackers put in to compromise a user's device—their intent is to profit from it. They go wherever they believe they can make the most money." And if that happens to be your phone, you better be careful that your data doesn't end up held for ransom.
Follow us on Google News



![Some T-Mobile users might be paying more starting in March [UPDATED]](https://m-cdn.phonearena.com/images/article/176781-wide-two_350/Some-T-Mobile-users-might-be-paying-more-starting-in-March-UPDATED.webp)










Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: