Apple says researcher is wrong and the iPhone is not vulnerable to his brute force attack
Just yesterday, we told you about a way to get around the Apple iPhone's ten passcode attempt limit. Once you fail to open an iPhone after ten cracks at tapping in the correct passcode, the device is automatically wiped. This is done to prevent hackers from obtaining personal information stored in the handset. A researcher named Matthew Hickey said when an iPhone running iOS 11 is plugged in, keyboard input has precedence over the phone's passcode limit feature, which allowed him to design a method using brute force to open an iPhone.
With this in mind, Hickey said that trying all possible four-digit combinations from 0000 to 9999 in one string, and six-digit combinations from 000000 to 999999 in one string, would unlock a plugged in iPhone before it wiped all of the data. Hickey even made a video of the process.
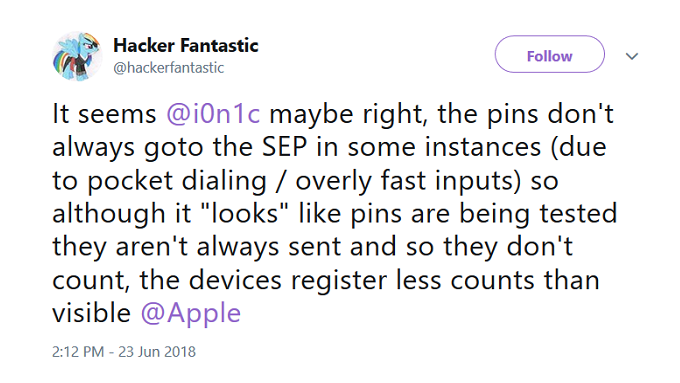
Apple has responded by calling Hickey's claims "erroneous." And support for the company's comments comes from a surprising source, the researcher himself. A new tweet from Hickey said, "the pins don't always goto the SEP in some instances (due to pocket dialing / overly fast inputs) so although it "looks" like pins are being tested they aren't always sent and so they don't count, the devices register less counts than visible." In other words, not all of the passcodes are actually being registered when sent in a long string. No third parties have been able to duplicate Hickey's original claim.
Apple is looking to batten down the hatches with iOS 12. The new build's USB Restricted Mode will prevent the Lighting port on an iPhone from communicating with other devices if that specific iPhone is not unlocked (using the correct passcode) within the last hour. Apple originally designed this feature to prevent cracking machines like the GrayKey from using an iPhone's Lightning port to disable the ten passcode attempt limit. The company behind that machine, Grayshift, says it has already figured out a way to defeat iOS 12's USB Restricted Mode.
"The recent report about a passcode bypass on iPhone was in error, and a result of incorrect testing."-Apple
Follow us on Google News













Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: