Grayshift says it has defeated Apple's USB Restricted Mode allowing it to crack open any iPhone
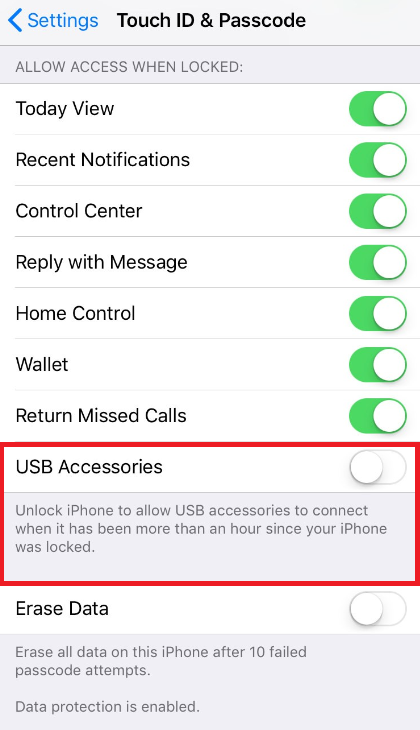
Settings screen that shows how an iPhone user can disable USB Restricted mode
But before Apple could say "checkmate," Grayshift, the company that manufacturers the GrayKey cracking machine, says that it has already defeated the upcoming USB Restricted Mode. If true, that puts the ball squarely in Apple's court as pressure will mount inside Cupertino to respond with another way to prevent these machines from opening an iPhone so that law enforcement and hackers can access personal data inside it.
According to Motherboard, an email it has seen was sent this month by a forensics expert who was supposed to meet with Grayshift. The email says that Grayshift claims that it has defeated the Restricted USB Mode feature in a beta build of iOS 12. Additionally, the company made it clear that the GrayKey has many capabilities that it will be able to use in the future to stay one step ahead of Apple.
"Grayshift has gone to great lengths to future proof their technology and stated that they have already defeated this security feature in the beta build. Additionally, the GrayKey has built in future capabilities that will begin to be leveraged as time goes on."-Email from unnamed forensics expert
While Grayshift appears confident in its ability to defeat USB Restricted Mode, rival Cellebrite, not so much. VP of research at the Israeli firm, Shahar Tal, sent out a tweet today that read, "tmw (That moment when) 10 of the last 12 threads in my inbox have 'USB Restricted Mode' in the subject line, and you realize it's just the beginning."
source: Motherboard
Follow us on Google News










![A new Android bug is making it impossible to install new apps. Are you affected? [UPDATE]](https://m-cdn.phonearena.com/images/article/176703-wide-two_350/A-new-Android-bug-is-making-it-impossible-to-install-new-apps.-Are-you-affected-UPDATE.webp)
Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: