Serious Safari bug reveals iPhone, iPad, and Mac users' personal data

Security firm FingerprintJS (via 9to5Mac) published a report on Friday about a bug found in the iOS 15 version of the Safari mobile browser. The report states that this bug "lets any website track your internet activity and even reveal your identity." A bug found in an Application Programming Interface (API) used and supported by most browsers could be used by attackers to find out many things about you.
An API is used by programmers to connect parts of the software to other software making it easier to develop programs. One such API, called IndexedDB, is supported by most major browsers and holds what the report calls "a significant amount of data."
Safari on iOS 15 and iPadOS 15 has a bug that can be exploited to reveal your personal data
The bug in the iOS 15, iPadOS 15, and macOS allows random websites to know what other sites a user is visiting on other windows and tabs. That is possible because sites like YouTube, Google Calendar, and Google Keep use "unique user-specific identifiers" in their database names. As a result, authenticated users can be identified as the aforementioned sites create databases that include the Google User ID belonging to the user, and databases are opened for all the accounts being used.
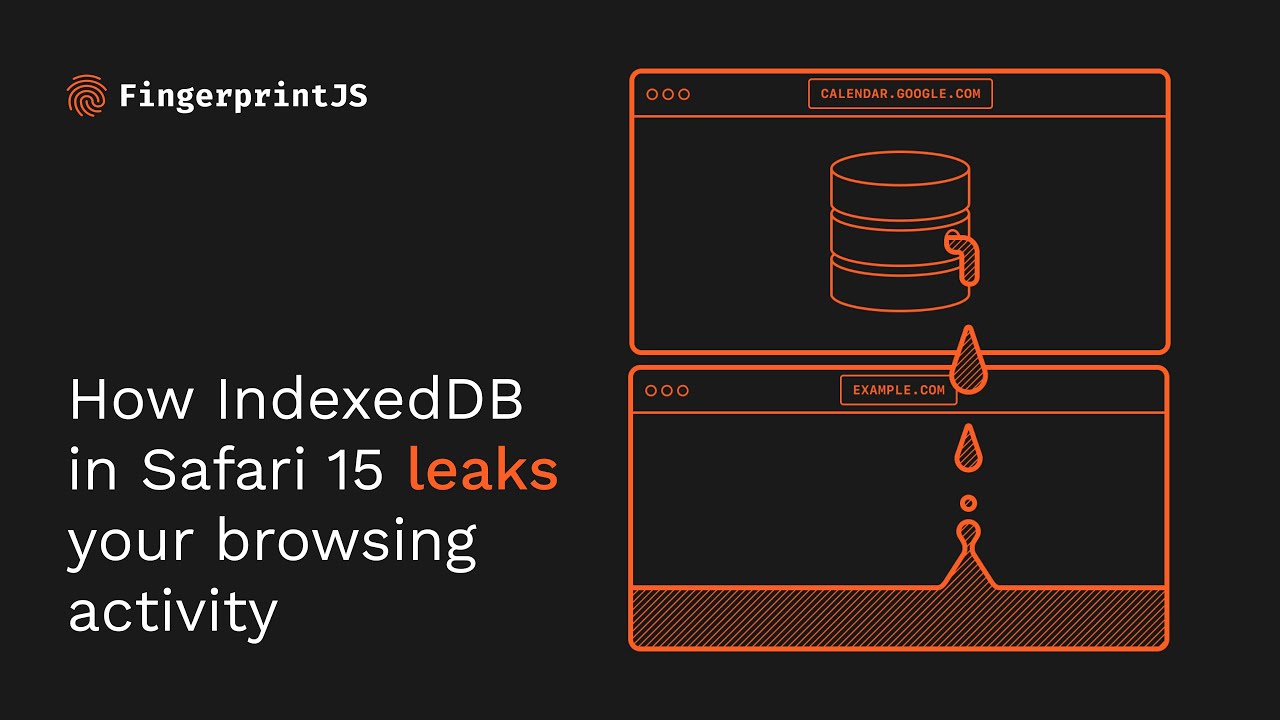

The Google User ID leads an attacker to a wealth of personal data. Each one can be used to identify a specific Google account and in combination with Google APIs, it can, at the least, reveal your profile picture to a hacker. It also could help the attacker grab much more personal information and unravel "multiple separate accounts" owned by the same user.
Unfortunately, learning your personal information doesn't require you to perform any specific action as the report states "A tab or window that runs in the background and continually queries the IndexedDB API for available databases, can learn what other websites a user visits in real-time. Alternatively, websites can open any website in an iframe or popup window in order to trigger an IndexedDB-based leak for that specific site."
FingerprintJS checked with Alexa's top 1,000 visited sites and found that 30 interact with indexed databases right on their homepage, without any interaction or authentication required by the user. Even if a person is using the private mode in Safari, if he visits multiple websites using the same tab, all databases interacted with are leaked to the sites the user subsequently visits.
Is there a way to avoid this bug?
There isn't much that a Safari user can do if he is running iOS 15 or iPadOS 15. One suggestion is to block all JavaScript by default and only allow it on sites that are 100% trusted. Mac users can switch browsers to escape this bug, but this is not a solution on iOS 15 or iPadOS 15. We should point out that the bug was submitted by FingerprintJS to the WebKit Bug Tracker on November 28, 2021, as bug 233548.
If you want to check this out on your iPhone or iPad, open Safari and point it at safarileaks.com and follow the simple directions. Quickly (too quickly), the name of the last site you visited appears (if it was one of the sites listed on the Demo page) and your unique Google User ID can be accessed.
Frankly, the only solution that you have is to wait for Apple to update the iOS and iPadOS software and make sure to install it as soon as it is released. Again, if you're using a Mac, changing browsers is a valid option although that is not the case with iOS and iPadOS. And keep in mind that users don't need to perform any specific action in order to set off the bug.
Follow us on Google News













Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: