Apple employee failed to immediately report zero-day Chrome vulnerability to Google
A zero-day vulnerability is a software flaw that was unknown to the developer or vendor before they were alerted about it; this means that they had "zero-days" to fix it. Normally, a company that finds a zero-day vulnerability would tell the developer or the vendor even if they worked for a rival outfit. Why? Because it helps stop a malicious hacker, it helps clean up the industry, and because the company never knows when it might be on the other side of such a situation.
The other day, per 9to5Mac, an Apple employee discovered a zero-day vulnerability in Google Chrome but did not immediately report it to Google. When discussing the update to the Chrome Browser to fix the zero-day vulnerability, Google pointed out that the bug was discovered during a hacking competition called "Capture The Flag" (CTF) back in March. And now Google has patched the flaw although it can't thank Apple for pointing out the issue to it.
So how did Google find out about the Zero-day vulnerability hanging over the head of its Chrome Browser? A Google employee wrote in a blog (via TechCrunch) that another participant in the CTF competition reported the bug on March 26th. What he wrote was that "This issue was reported by sisu from CTF team HXP and discovered by a member of Apple Security Engineering and Architecture (SEAR) during HXP CTF 2022."
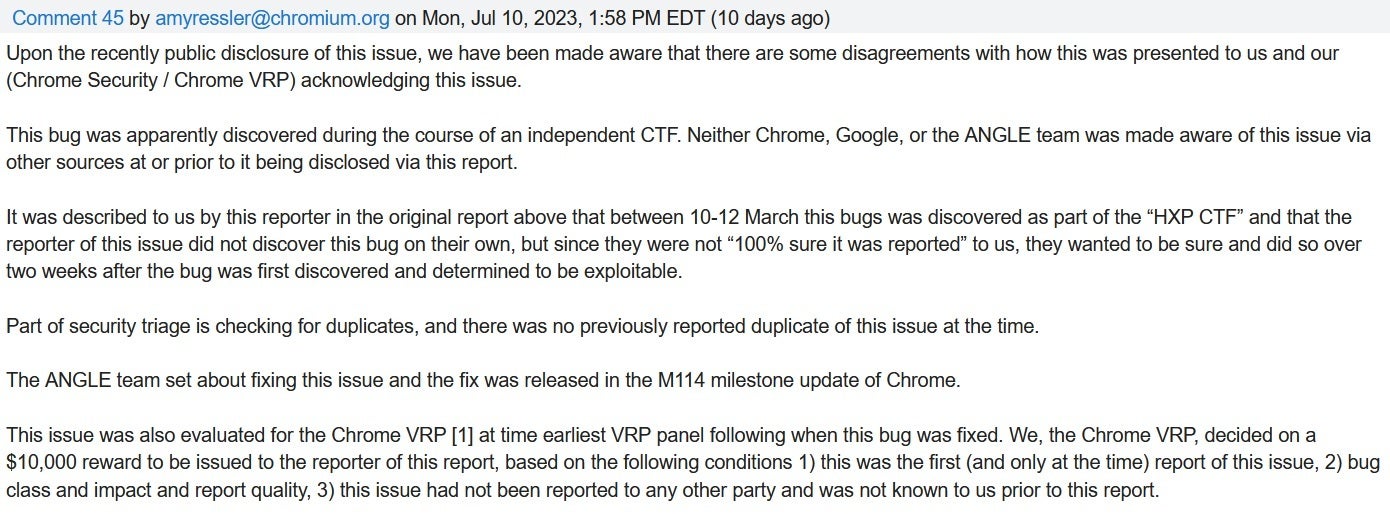
Google reveals the story on the chromium bugs site
TechCrunch eventually found a Discord channel where someone who claimed to be the Apple employee who found the vulnerability explained why he did not report it to Google. The person, who goes by the name of Gallileo, wrote on July 6th, "It took me 2 weeks working on it full time to root cause, write [the] exploit [Proof of Concept] and writeup the issue such that it can be fixed."
He went on to say that the flaw "...was reported on June 5th, through my company. Yes it was late, there are multiple reasons for that. I first had to find the person responsible, the report had to be signed off by people and then the person responsible was OOO (out of the office). It’s commendable that Chrome decided to fix it asap, but I think there wasn’t any real urgency. Only you and my team was aware of it and the issue is likely not that great in a real-world scenario (doesn’t work on Android, pretty visible since it freezes the Chrome GUI for a few seconds."
The original report, as noted, was dated March 26th and Google decided to reward the person who brought it to their attention with a "bug bounty" of $10,000. Who says that it doesn't pay to be a bug exterminator? Also, it's not unusual for flaws to be discovered during "Capture the Flag" hacker competitions.
The original report, as noted, was dated March 26th and Google decided to reward the person who brought it to their attention with a "bug bounty" of $10,000. Who says that it doesn't pay to be a bug exterminator? Also, it's not unusual for flaws to be discovered during "Capture the Flag" hacker competitions.
Follow us on Google News













Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: