Russian hackers using Instagram to mask malware links

The last place one'd expect to encounter malware would be at a celebrity's social profile.
Turla, a Russian hacking collective, was recently found to be using Instagram comments as a means of hiding links to its malware. Known for targeting governments in the past, the hacker group appears to be experimenting with familiar routes of infection, although targeting rather unfamiliar victims – everyday citizens. By planting encoded links to their malware within the comments section of a photo on Britney Spears’ official Instagram page, hackers were able to infect some visitors with malware. Fortunately for most Instagram users, this particular attack only affects those accessing the website through Firefox’s full desktop web browser, rather than Instagram’s mobile app. Additionally, a malicious extension by the name of “HTML5 Encoding 0.3.7” needed to have been previously installed for the malware to be effective. By nature of such an attack, the hidden links to malware were not clickable or otherwise able to activate without this extension.
While the Firefox extension is best removed immediately if present, Britney Spears’ Instagram should be otherwise safe to visit. Without a malicious extension installed to piece together the link, the comment is as harmless and innocuous as Britney’s music itself.
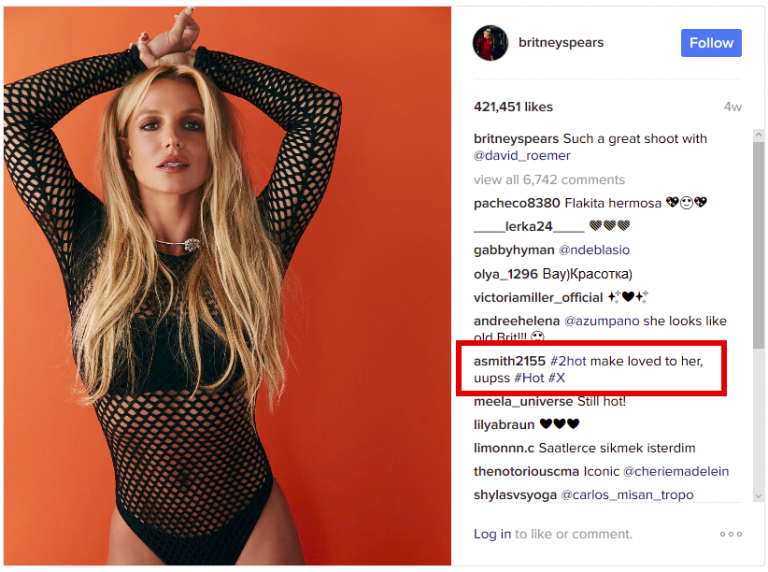
User comment concealing a malicious link
Threats like this one are known as a “watering hole attacks.” By lacing a common website (the figurative watering hole) with concealed links to malware, hackers can attack visitors without their knowledge, typically exploiting a vulnerability in software to do so. In this instance, the vulnerability was not in Firefox itself, but rather the bogus extension whose only purpose is to establish a backdoor. This extension could have been willfully downloaded by the user – likely from a compromised website telling unsuspecting visitors to do so – or installed through a previously deployed malware-laced Word document which was sent to various institutions via email. Whatever the route of transmission, the extension is installed, and a backdoor is created. Through this, an encoded link, such as the one found in these comments, can be deciphered and activated. This creates a covert connection between the user and the hacker’s malware servers not only allowing malware to be downloaded, but also enabling the upload of personal files or information to their servers.
On Tuesday, Senior Malware Researcher for ESET Antivirus, Jean-Ian Boutin released a report on the attack via ESET’s website.
“There were only 17 hits recorded on this link in February, right around the time the comment was posted. However, this is quite a low number and might indicate that it was only a test run … the next version of the extension – if there is one – is likely to be very different. There are several [components] that are used by the extension that will disappear in future versions of Firefox.”
In other words, most of the ways in which this threat operates will be nullified in the next version of Firefox, so keeping up to date is crucial.
Equally important is the use of some general practices to help avoid such attacks altogether.
These guidelines also apply to mobile platforms like iOS and Android, as well as their apps. While this particular attack hasn’t yet made it to phones, many mobile attacks have. Targeting social media shows interest in the public, and most of the public is on phones, so taking these simple precautions is highly advisable.
ESET researchers recommend keeping your browsers and their plugins up-to-date, but generally, having less extensions is always safer. Getting rid of those that may be unrecognized or unused is a worthy endeavor – one that could certainly protect your privacy. In the case of extensions which you absolutely need (or really enjoy) a little bit of research can go a long way. If you don’t instantly recognize the creator of the extension, as you may if it were made by Google or Twitter, for example, simply do some searching to find out, “is this extension safe?” For smaller, but still legitimate add-ons like Integrated Inbox, the evidence of a well-documented official website is a good start. Not every safe add-on will have a dedicated website though, so further research through Google or user reviews can lend valuable insight, as in the case of Integrated Inbox’s glowing reviews.
Checking the safety of the apps and extensions you download may not be the most fun part of your day, but at least then you can surf Britney’s Instagram [relatively] free of worry.
source: ESET via Arstechnica
“There were only 17 hits recorded on this link in February, right around the time the comment was posted. However, this is quite a low number and might indicate that it was only a test run … the next version of the extension – if there is one – is likely to be very different. There are several [components] that are used by the extension that will disappear in future versions of Firefox.”
In other words, most of the ways in which this threat operates will be nullified in the next version of Firefox, so keeping up to date is crucial.
Equally important is the use of some general practices to help avoid such attacks altogether.
- Avoid installing apps/programs/extensions from unknown authors
- Do not open documents or files of any kind that are sent to you from an unknown sender
- If a website says a certain download is required, do not use the link it offers, rather go to the website of the manufacturer and download the program from there. For example, go to Apple’s website to download iTunes, or Adobe’s to download Flash. If after the program is installed the website is still asking for it, you can be fairly certain this is an attempted attack.
- Search, search, search! If you’re unsure, Google it. Check app/program reviews, as well – not just star ratings, but the reasoning behind them if comments are in fact available.
These guidelines also apply to mobile platforms like iOS and Android, as well as their apps. While this particular attack hasn’t yet made it to phones, many mobile attacks have. Targeting social media shows interest in the public, and most of the public is on phones, so taking these simple precautions is highly advisable.
source: ESET via Arstechnica
Follow us on Google News










Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: