Latest Android vulnerabilities can brick your phone, control the camera, steal your cash, and more

We've discussed the "F" word before when talking about Android, and when it comes to the distribution of the monthly Android security update, fragmentation could be a serious problem for millions of Android users. That's because not every handset manufacturer pushes out the latest security patch in a timely manner. This is another example of why real fans of Android or the Google ecosystem might want to buy a Pixel (along with the fact that they get the first crack at the latest build of Android and cool features such as real-time transcription and Astrophotography).
Many Android phones, including a recently purchased Samsung Galaxy Note 10+ 5G (which comes out of the box with Android 10 at T-Mobile) did not include the December update. In a statement, Samsung said that "while we are doing our best to deliver the security patches as soon as possible to all applicable models, delivery time of security patches may vary depending on the regions and models." We can only imagine the list of Android phones that are months behind.
For the majority of Android users, the monthly security update is a snooze-fest since it doesn't make any changes or add new features that they can see or use. But the problem is that the December security update is important because of a vulnerability known as CVE-2019-2232. According to the NIST National Vulnerability Database (via Forbes), a maliciously written message could result in a permanent denial of service attack that would brick a phone running Android 8, 8.1, 9, or 10. The December Android security update includes a patch for CVE-2019-2232 which means that if the update has been sent to your phone, install it immediately. But again, the real problem is that only a limited number of devices have it at the moment. The update was first disseminated on December 2nd and Google says, "In general, it takes about one and a half calendar weeks for the OTA to reach every Google device." And that is just for the Pixel handsets.
"StrandHogg" is a dangerous vulnerability that puts the top 500 Android apps at risk
The reason for the fragmentation is that unlike Apple, which produces both the hardware and software for the iPhone, there are a large number of Android manufacturers. You can find which security patch you received last by going to Settings > About phone > Android version. Our Pixel 2 XL has the December 5th security patch level installed.
Many other security issues have recently cropped up for Android uses. Last month we told you about an issue with the Google Camera app that allowed a bad actor to remotely shoot videos and photos using the camera on an unsuspecting Android user's phone. The vulnerability affected hundreds of millions of Android users. Also last month, we passed along word of a vulnerability discovered in the next generation of Android messaging, Rich Communication Service (RCS). Attackers could have exploited this by spoofing caller ID and by phishing. In the worse-case scenario, an Android user might have be tricked into giving up PINs to bank and other accounts where significant assets would have been discovered and stolen.
Earlier this month, information about the "StrandHogg" vulnerability was released by security software developer Promon. Disguised as a legitimate app, this malware put the top 500 Android apps at risk (Promon partner Lookout discovered 36 malicious apps that actually carried the vulnerability) and allowed bad actors (without root access) to listen in on Android users through a phone's microphone, take control of the camera and remotely snap pictures, read and send SMS messages from a handset, make and record phone calls, learn a user's location through GPS access, see photos and files on an Android handset, view contacts, phone logs and more.
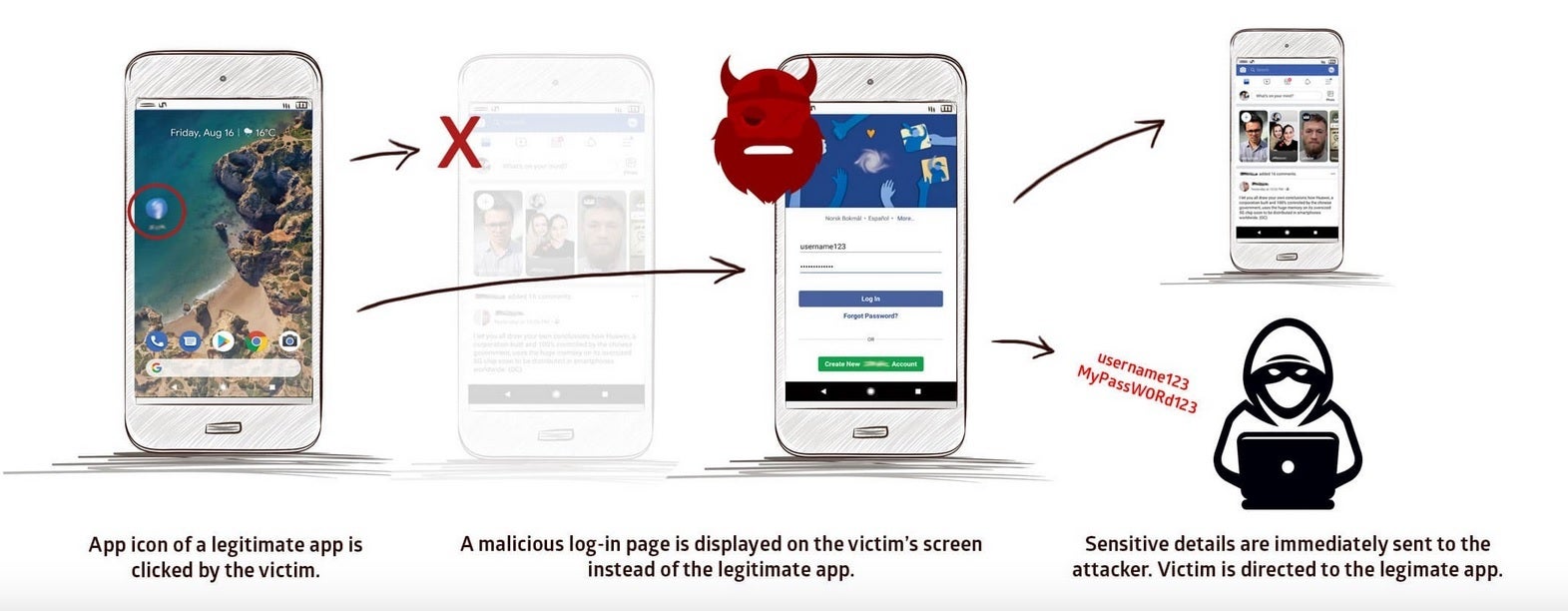
StrandHogg is a dangerous vulnerability that could give hackers access to your personal information
With "StrandHogg," an Android user would click on the icon belonging to a legit app. Instead of the legit app, malware would be displayed asking for certain permissions. Once these permissions were granted by the unsuspecting Android user, the hacker was given the green light to hack away. This vulnerability could unleash a phishing attack allowing the bad actor to obtain important personal data.
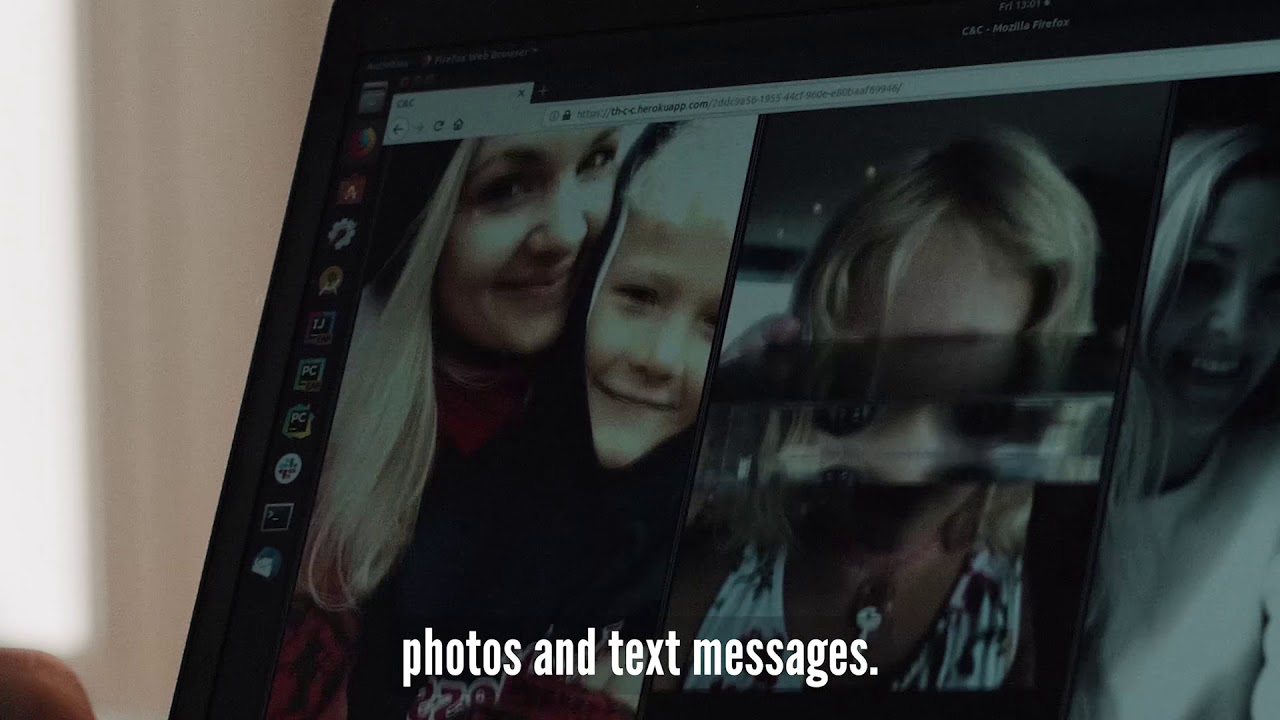

Google recently announced that it was teaming up with some security firms (including the aforementioned Lookout) in an attempt to fight back against malware. Hopefully, the App Defense Alliance can get one step ahead of the bad actors. The security research firms typically contact Google with their findings and the company closes these vulnerabilities. However, with StrandHogg, Promon notes that Google did not take it seriously at first and while it eventually removed the apps responsible for distributing the malware, this vulnerability has apparently not been fixed. And many of the "dropper apps" that helped spread StrandHogg are still on Android users' phones. One, a PDF creator app named CamScanner, has been installed over 100 million times.
Follow us on Google News












Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: