How Android N is being built to prevent the next Stagefright

What makes you chose one smartphone platform over another? App selection? Hardware availability? System security is another big factor shoppers take into consideration, and last year Google suffered a PR nightmare after the publication of the Stagefright attack, a vulnerability with the double whammy of presenting a serious risk to users, and being exploitable on a huge fraction of Android devices out there. With Android N, Google's getting serious about preventing another Stagefright disaster, and today shares some of the ways it's going about preventing another such attack.
Remember, Stagefright worked through the creation of specially formed media files; when Android's media subsystem attempted to process these files, the bug seized control of that software, gaining the ability to execute its own malicious code in the process.

For example, if a bug got control of the old MediaServer, it could access the Android file system, communicate over the network, and read and write to system memory - all bad stuff in the wrong hands. By compartmentalizing things in Android N (see chart below), Google's making sure that even if something like a malicious audio file seizes control of MediaServer, it can only do other audio-related things; it might mute your phone or mess with your Bluetooth connections, but it's not going to be able to take control of the full system.
Well, that's the plan, anyway. Hackers are a resourceful bunch, and it remains to be seen just how well these steps will actually keep Android N safe. For now, we're just glad that Google's trying to stay ahead of the curve, being proactive rather than reactionary.
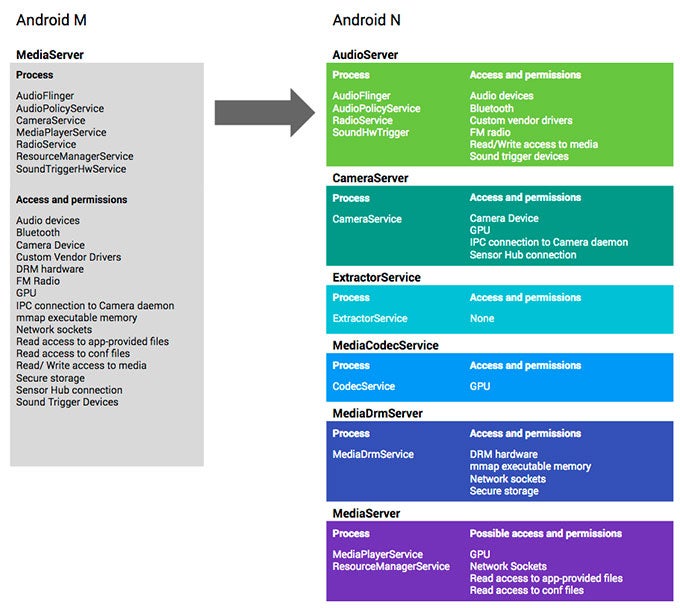
How Google's limiting bug fallout by splitting up permissions
source: Google
Follow us on Google News











Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: