Apple's updated security reports show the iPhone had more vulnerabilities than first revealed
Last week we told you that Apple released iOS 16.3.1 and iPadOS 16.3.1 to patch a couple of software flaws. One vulnerability was found in the WebKit browser engine that was given the Common Vulnerabilities and Exposures (CVE) number 2023-23529. This flaw could allow an attacker to take advantage of arbitrary code execution that would allow the hacker to execute commands on a target device. Apple said that it was aware of a report that this vulnerability may have been actively exploited.
The iOS 16.3.1 update also fixed a vulnerability in the Kernel that could allow an app to execute arbitrary code with kernel privileges. Apple patched this flaw with improved memory management.
Today, Apple belatedly added another vulnerability (CVE-2023-23524) that was patched by iOS 16.3.1 and iPadOS 16.3.1. This flaw could have allowed an attacker to allow an iPhone or iPad to process a "maliciously crafted certificate" which would lead to a denial-of-service (DoS) attack. These attacks flood the network with bogus traffic causing a crash and preventing legitimate users from being able to access the information they need or to complete the actions that they were trying to accomplish. Apple fixed the flaw with "improved input validation."
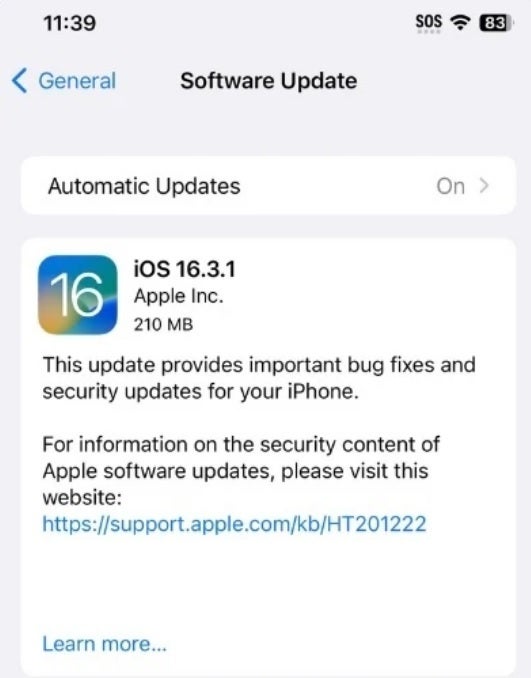
Apple added more information about security patches that were part of iOS 16.3 and iOS 16.3.1
Per 9to5Google, Apple went back to the iOS 16.3 and iPadOS 16.3 security content support page and added three new flaws that were patched with iOS 16.3 and iPadOS 16.3. One, CVE-2023-23520, was found in the iOS Crash Reporter which could allow attackers to read arbitrary files as root. Two other vulnerabilities, CVE-2023-23530 and CVE-2023-23531, were also added to the security content support page.
Both of these flaws were found on the iPhone and iPad's Foundation which Apple says, "provides a base layer of functionality for apps and frameworks, including data storage and persistence, text processing, date and time calculations, sorting and filtering, and networking." With improved memory handling, Apple was able to patch the vulnerability which could have allowed an app "to execute arbitrary code out of its sandbox or with certain elevated privileges."
A sandbox for an app restricts an app from obtaining or changing files used by other apps. It also prevents apps from making changes to a device. Allowing an app to execute commands out of its sandbox could be extremely dangerous and might allow an attacker to gain complete control over an iPhone or iPad.
To make sure that you've downloaded the latest software on your phone, go to General > Software Update and follow the directions.
Follow us on Google News













Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: