Security flaw discovered on Samsung Galaxy devices, (kind of) allows lock screen bypassing
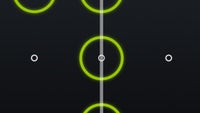
Although the following vulnerability is not likely to expose any sensitive data stored on one's smartphone, its a flaw that must be brought to people's attention. It has been discovered that the Samsung Galaxy Note II, Galaxy S III, and perhaps other of the maker's recent Android smartphones running version 4.1.2 of the OS are affected by a glitch that exposes their home screen for a fraction of a second even if the device is protected by a PIN or pattern.
The video below demonstrates how the hack is performed by accessing the "Emergency Call" menu from the pattern lock screen and then listing the user's ICE emergency contacts list. If the home button is pressed at that time, the home screen is displayed briefly, thus letting one launch applications, assuming their fingers are fast enough. In theory, that could allow someone to call contacts listed on Direct Dial widgets, or cause other kinds of trouble. We can confirm that the hack works on a Samsung Galaxy S III running Android 4.1.2.
Of course, the flaw is no cause for major panic, but it is one that definitely shouldn't be present on a device that is supposed to be secure. In case someone can confirm the presence of this vulnerability on other Samsung Android devices, let us know down in the comments!
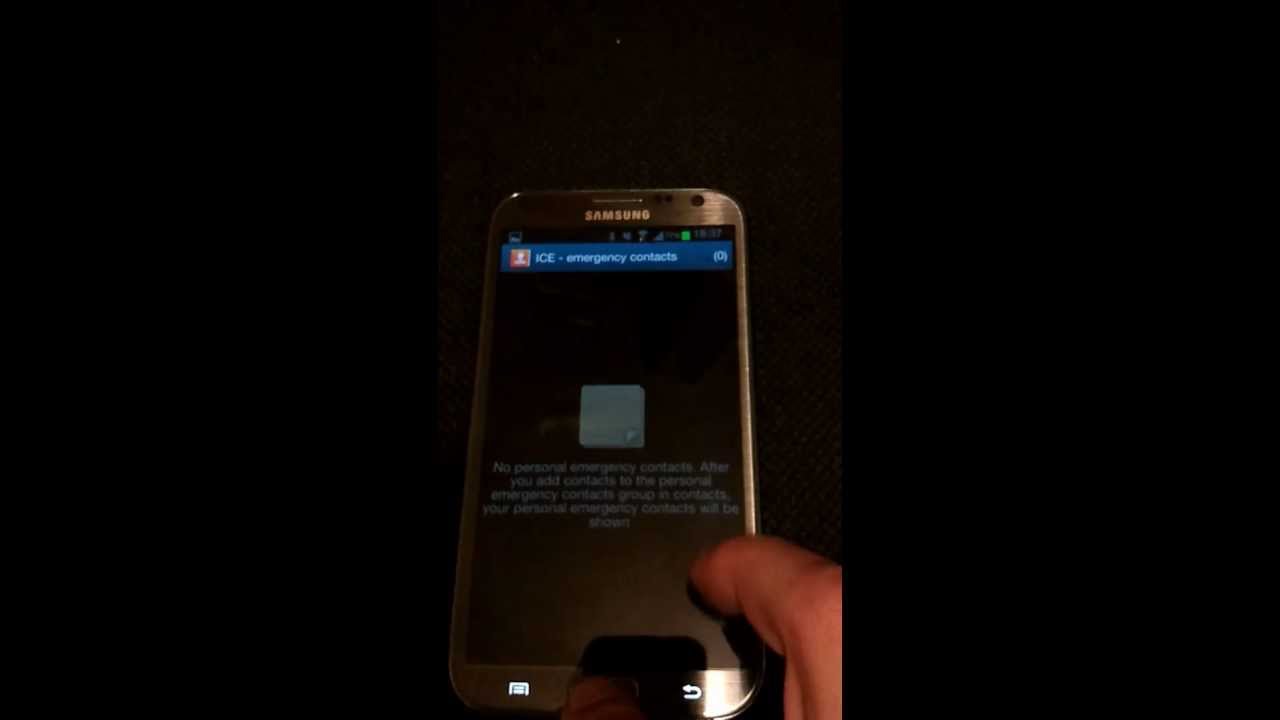
source: Terence Eden via Engadget
Follow us on Google News











Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: