Passwords stored on a locked iPhone retrieved for six minutes using off-the-shelf exploits

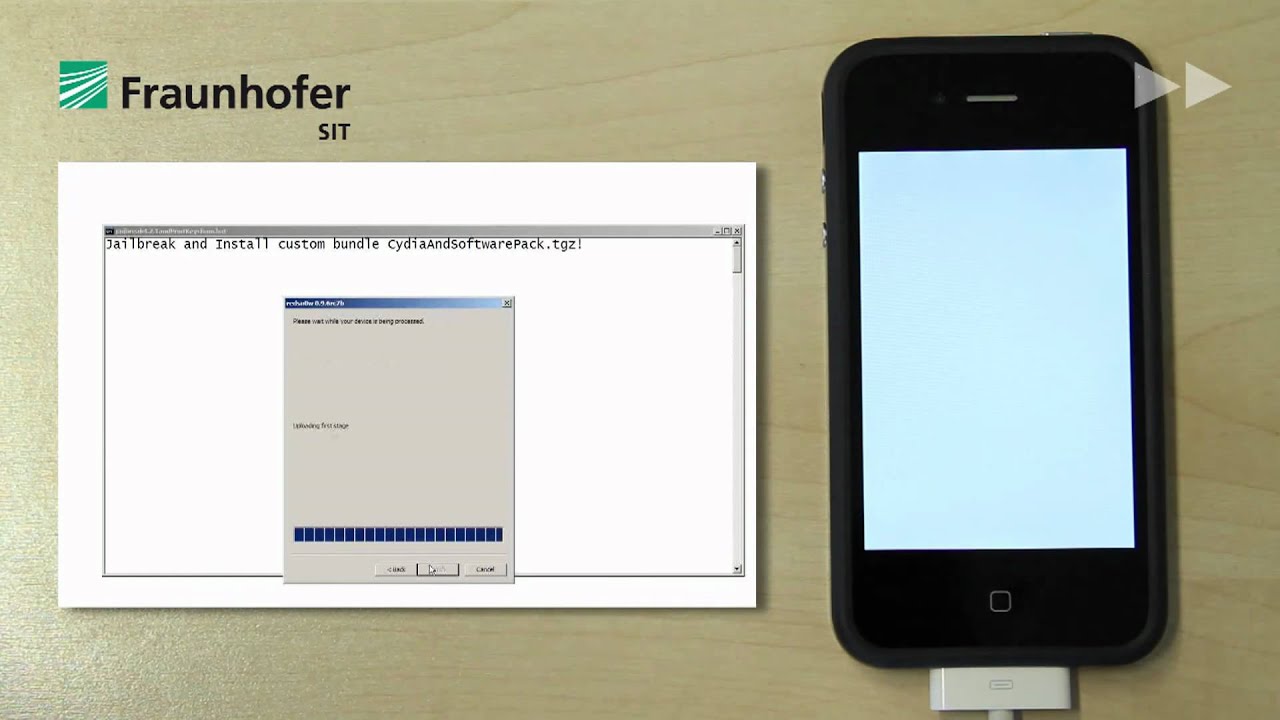
Researchers at the Fraunhofer Institute in Germany were able to retrieve a number of passwords from a locked iPhone, using known exploits. Instead of crunching the passcode, they jailbroke the device first, and then installed an SSH server on the phone that allows running software on it.
Then the researchers copied a Keychain (Apple's password management system) access script, and executed it to ultimately spill out the account passwords which are stored there. It was possible, because the cryptographic key is based on code you can find in the iOS device itself, and is not tied up to the passcode.
Thus the guys from the Fraunhofer Institute managed to retrieve the Gmail, Wi-Fi and some apps passwords, as well as the MS Exchange pass and the corporate VPN access code. The last two are particularly troubling, considering Apple is fighting hard to spearhead iOS devices adoption in the enterprise, even poaching talent from RIM.
To add insult to injury, it took the researchers a whole of six minutes with physical access to the phone to retrieve all of the above info. They even recorded it on video, so if someone didn't know before how to do it, now they can.
source: PCWorld
To add insult to injury, it took the researchers a whole of six minutes with physical access to the phone to retrieve all of the above info. They even recorded it on video, so if someone didn't know before how to do it, now they can.
source: PCWorld

Follow us on Google News













Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: