Data moving between your smartwatch and phone can be easily stolen
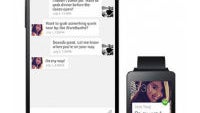
While we have been getting quite a bit of good news today when it comes to wearables, and specifically the Android 5.0 Lollipop update coming to Android Wear smartwatches, there is also some bad news to pass along. It turns out that the data moving between your smartwatch and smartphone is not secured very well, and can be easily stolen.
The exploit was recently proven by Bitdefender using a Samsung Gear Live and a Google Nexus 4 running a preview version of Android 5.0. The exploit gains access, because Bluetooth's PIN number pairing method is easily overcome by a brute force attack, since there are only one million possible PIN combinations. The hacking tools are easily found, and once the PIN is found through a brute force attack, any data moving between your smartwatch and phone can easily be captured. A lot of the data currently being passed between your wearable and phone is relatively useless, like weather, sports scores, or generic app alerts. But, it also leaves any messaging or calendar event data open to be stolen.

Android Wear currently relies on your smartwatch co-processor to handle encryption, but that is easily overcome, according to Bitdefender. A change to the way Bluetooth authenticates a pairing connection could help fix the problem, like a move to NFC authentication for Bluetooth pairing, so a brute force attack wouldn't be possible. But, a fix will take time to get sorted out, and your data could be at risk in the meantime.

source: Hot for Security via Ars Technica
Follow us on Google News













Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: