You might be using a hacked Dell laptop right now, and wiping Windows won't save you
Affecting 100+ Latitude and Precision models, this exploit slips right past antivirus protection.
Dell Latitude 5450. | Image by Dell
A new report reveals that more than 100 Dell laptop models, mainly from the Latitude and Precision lines used by enterprises, cybersecurity experts and government agencies, are affected by a set of critical firmware vulnerabilities. These flaws could give attackers persistent access – even if you wipe and reinstall Windows.
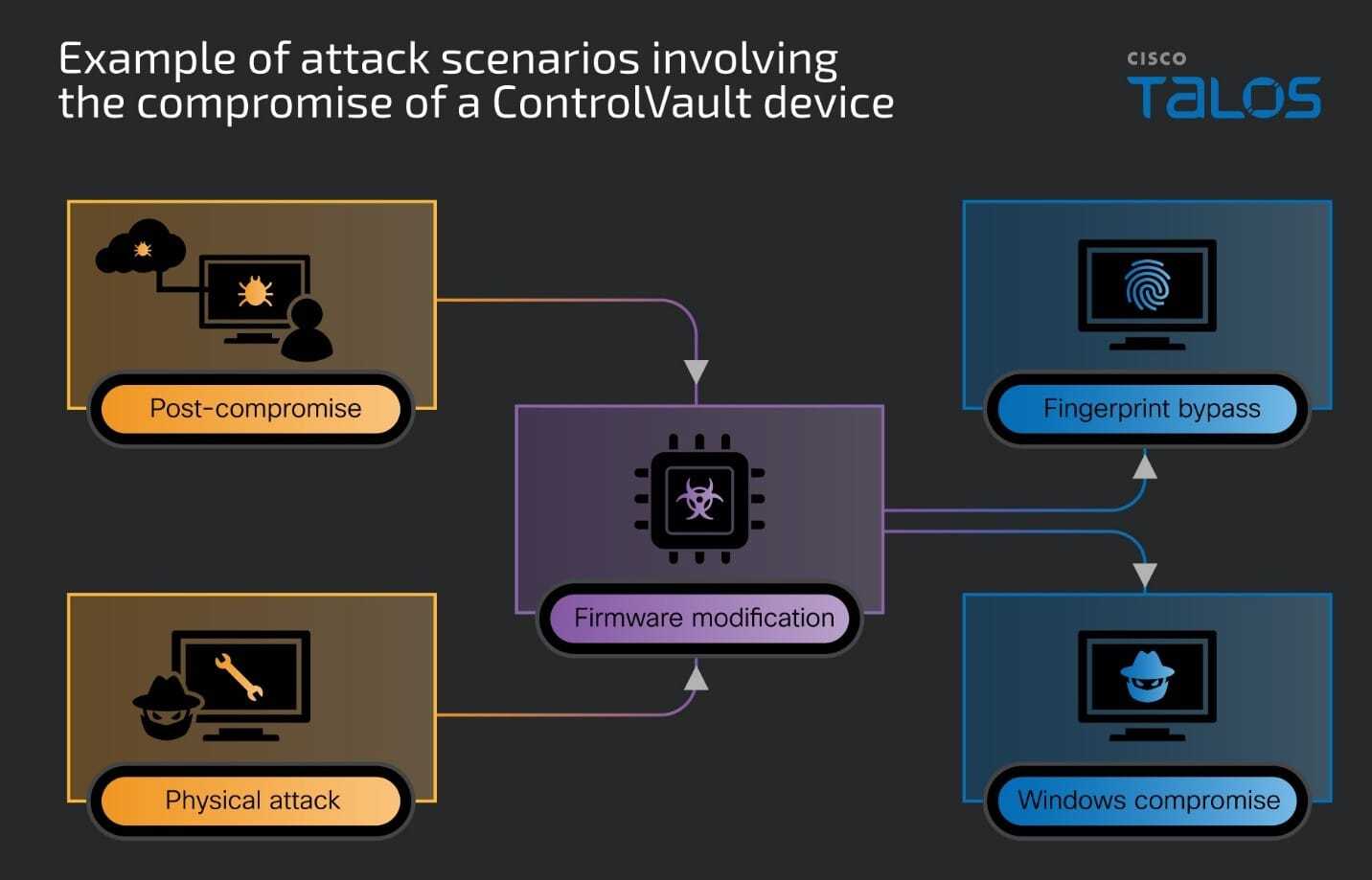
This is how a device could be compromised.
Dell has confirmed the vulnerabilities and rolled out security updates, but if you are in charge of managing a fleet of Dell machines, now is the time to make sure those updates are actually getting installed.
What's ControlVault3 and why does it matter?
Dell's ControlVault is a hardware-based security system – a kind of digital vault – that stores your most sensitive info, like passwords, fingerprints and security codes, outside of your regular OS. It lives on a separate board inside the laptop called the Unified Security Hub (USH) and connects to smart card readers, NFC and fingerprint scanners.
Cisco Talos researchers found five major flaws in ControlVault3 and ControlVault3+ firmware:
- CVE-2025-24311 – Out-of-bounds read → info leak
- CVE-2025-25050 – Out-of-bounds write → code execution
- CVE-2025-25215 – Arbitrary memory free → memory corruption
- CVE-2025-24922 – Stack-based buffer overflow → code execution
- CVE-2025-24919 – Unsafe deserialization in Windows APIs
Would you know if your laptop had a security flaw like this?
Honestly, probably not.
33.33%
Only if it made the news.
13.33%
Yeah, I stay on top of firmware updates.
40%
I rely on IT/security teams for that stuff.
13.33%
The worst part? These flaws can survive a full Windows reinstall.
Because the vulnerabilities sit below the OS in the firmware layer, they can give attackers persistent access – and antivirus software won't catch it. The research team showed how even non-admin users can trigger these flaws through Windows APIs, potentially stealing cryptographic keys and modifying the firmware itself.
And even without remote access, an attacker with just a few minutes of physical access could open the laptop and connect directly to the USH board via USB, bypassing system login and even full-disk encryption.
What should users and admins do?
First, update now. Dell has been releasing firmware patches and drivers since March 2025 and in many cases, they are being pushed through Windows Update.
The researchers also recommend:
- Disabling ControlVault services/devices if you are not using fingerprint, smart card, or NFC readers.
- Turning off biometric login when leaving your laptop unattended.
- Using Enhanced Sign-In Security (ESS) in Windows for extra protection against physical tampering.
- Enabling chassis intrusion detection in BIOS, if available.
Also, endpoint detection tools could help flag suspicious firmware access attempts, and unexplained crashes in Windows Biometric or Credential Vault services could be signs something's wrong.
Why this matters more than ever
Firmware components like ControlVault are full computing systems on their own – they've got memory, processors and software. And that means attackers exploiting them can sidestep traditional OS-level protections completely.
These findings highlight the importance of evaluating the security posture of all hardware components within your devices, not just the operating system or software…
– Cisco Talos researchers, August, 2025
Follow us on Google News










Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: