How you can avoid having your bank account wiped out by an Android banking Trojan

The Godfather Android banking Trojan has a deal that you better refuse. A Trojan is a malicious app that pretends to be legitimate. It might actually perform the tasks that led you to install it in the first place until it receives its orders from a Command & Control (C&C) server. A banking Trojan goes after the information and data you use to sign into your banking apps and with that info in hand, it gets into your bank accounts and causes major headaches for you.
The Godfather banking Trojan has targeted more than 400 banking and crypto apps in 16 countries
According to cybersecurity firm Group-IB (via The Hacker News), the Godfather Banking Trojan has targeted over 400 banking and cryptocurrency apps in 16 countries. Between June 2021 and October 2022 when the Godfather banking Trojan was active, half of the targeted apps were banking apps while others attacked included cryptocurrency wallets and exchanges. 49 of the targets were American companies, 31 were Turkish and 30 were located in Spain. Financial service companies in Canada, France, Germany, the U.K., Italy, and Poland were also affected.
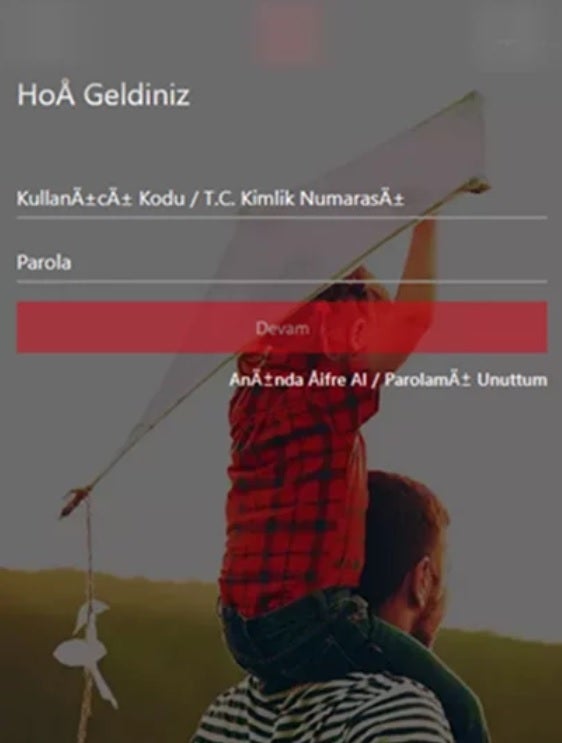
Fake Turkish banking app waiting to collect a victim's login information
When an Android user interacts with a phony notification or tries to open a legitimate app targeted by the Trojan, a fake overlay appears on the screen collecting usernames and passwords typed by the victim on his phone. The victim is tricked by the overlay into thinking that this information is required to open the infected banking or financial services app. Godfather can also bypass two-factor authorization making it extremely dangerous.
Group-IB says that the banking Trojan is being distributed via "decoy applications" listed on Google Play. As of October 2022, 215 international banks, 94 cryptocurrency and 110 crypto exchange platforms have been victimized by Godfather in the United States, Turkey, Spain, Canada, Germany, France, and the U.K.
Interestingly, Godfather seems to back down from infecting phones that list a language spoken in a post-Soviet country as a preference. Those countries include Russia, Azerbaijan, Armenia, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Uzbekistan, and Tajikistan. That leads Group-IB to believe that the developers of the Trojan speak Russian. The Trojan has also been known to record the victim's screen, send fake text messages from an infected device, and more.
One malicious app that was hosted in the Google Play Store linked to the Godfather banking Trojan is Currency Converter Plus. It has been discovered from samples of the Godfather Trojan that when the malware is open, a fake version of Google Protect appears with animation that makes the victim think that the app is being scanned when in reality, nothing is happening. And making matters worse, the app's icon hides and can't be seen in the list of a phone's installed apps.
Here are the steps to take to protect your Android phone from a banking Trojan
So with the user duped into thinking that the app has been scanned and no malware discovered, he opens his banking app, uses his login, and has just given the bad guys the key to his vault. But you can take certain steps that could help you fight back against banking Trojans like Godfather.
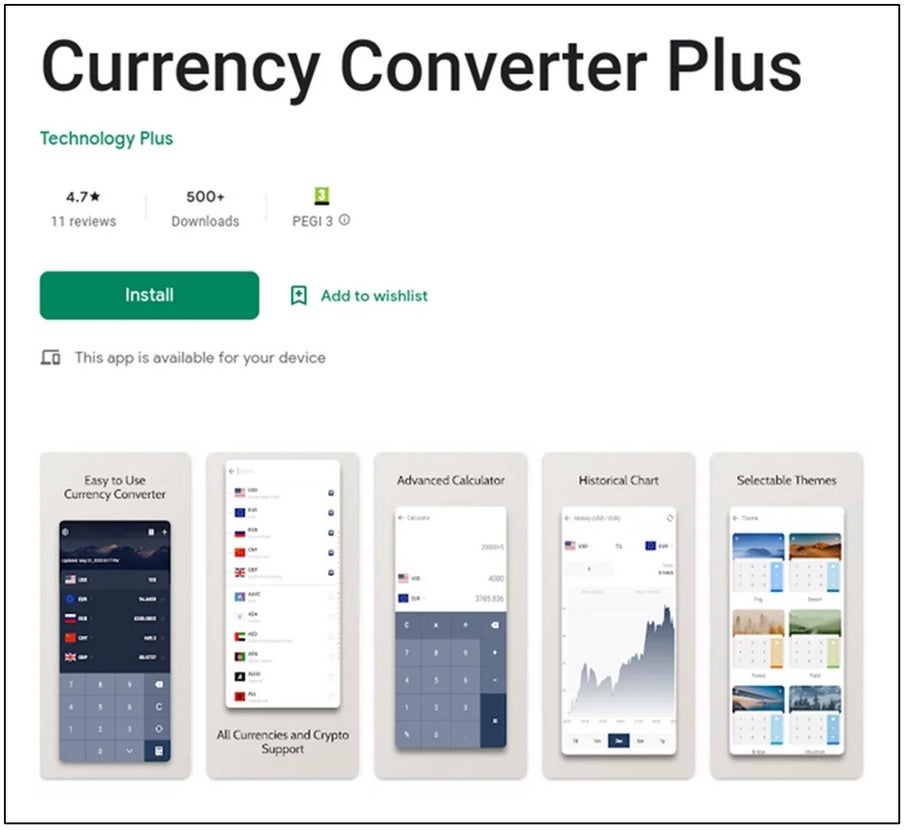
Malicious app once listed in the Google Play Store
According to Group-IB, always make sure that you are running the latest version of Android on your phone. The more recent the version of Android running on your phone, the less likely it is to be infected by a banking Trojan.
Group-IB also suggests that you do not sideload and install apps from third-party Android app storefronts even though Google cannot guarantee that every app is safe. The cybersecurity firm also suggests that you look at the permissions each app is asking for. If the permissions a specific app requests seem out of place, such as a request by a news app to use your microphone or camera (especially for an app with an unfamiliar developer), perhaps you should not install it. Also, do not click on links sent to you in text messages.
What can you do if your phone is already infected? Group-IB says to take the following three steps:
- Disable network access.
- Freeze any bank accounts that may have been accessed from your device.
- Contact experts to receive detailed information about the risks that the malware could pose to your device.
Follow us on Google News












Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: