Machines anyone can buy on eBay should worry iOS and Android users

Need to break into a locked Apple iPhone, or Android smartphone? Purchasing a hacking tool from Cellebrite, the Israeli firm that sells them to law enforcement, businesses and the military, will normally cost $6,000 and up for a new box. If you can't afford to purchase a new Cellebrite machine, you might be able to find one on eBay for as little as $100.
The company became famous in 2016 when a court ordered Apple to unlock an iPhone 5c belonging to San Bernardino shooter Sayed Farrok. Apple refused to do so, saying that it would have to create a whole new version of iOS in order to comply. The company worried that such software could be stolen by hackers. Eventually, the FBI said that it paid another firm, believed to be Cellebrite, to unlock the phone. The agency found no useful information inside Farook's iPhone 5c.
Apparently, former Cellebrite users needing to raise cash are selling them on eBay for prices as low as $100, despite pleas from the company not to do so. Cellebrite is concerned that equipment purchased from the online auction site could be used to illegally break into people's phones. And they are also concerned that a Cellebrite machine not properly wiped could offer up a treasure trove of information related to the previous use of a specific machine.
For example, one researcher who purchased a dozen of these boxes found data on them revealing the names of the devices that they were used on, the date when this took place, and these phones' unique IMEI numbers. The latter can be used to track down any of the phones that the previously owned Cellebrite machines were used on. Chats and contact lists can also be found on previously used hacking boxes.
A Cellebrite rival, GrayShift, has a similar box called GrayKey that uses a technique called "brute force" to unlock iPhones. With this process, the box runs through all possible combinations of numbers and letters to find the correct combination. The device is plugged into an iPhone's Lightning port to unlock it. In iOS 12, Apple launched USB Restricted Mode, which restricts the use of the port to communicate with another device if the phone has not been unlocked for over an hour. GrayShift said last summer that its box has other capabilities to tay one step ahead of Apple.
If regular people are picking up Cellebrite and other cracking devices on the cheap, it doesn't bode well for those who expect the information they put on their phones to remain private.
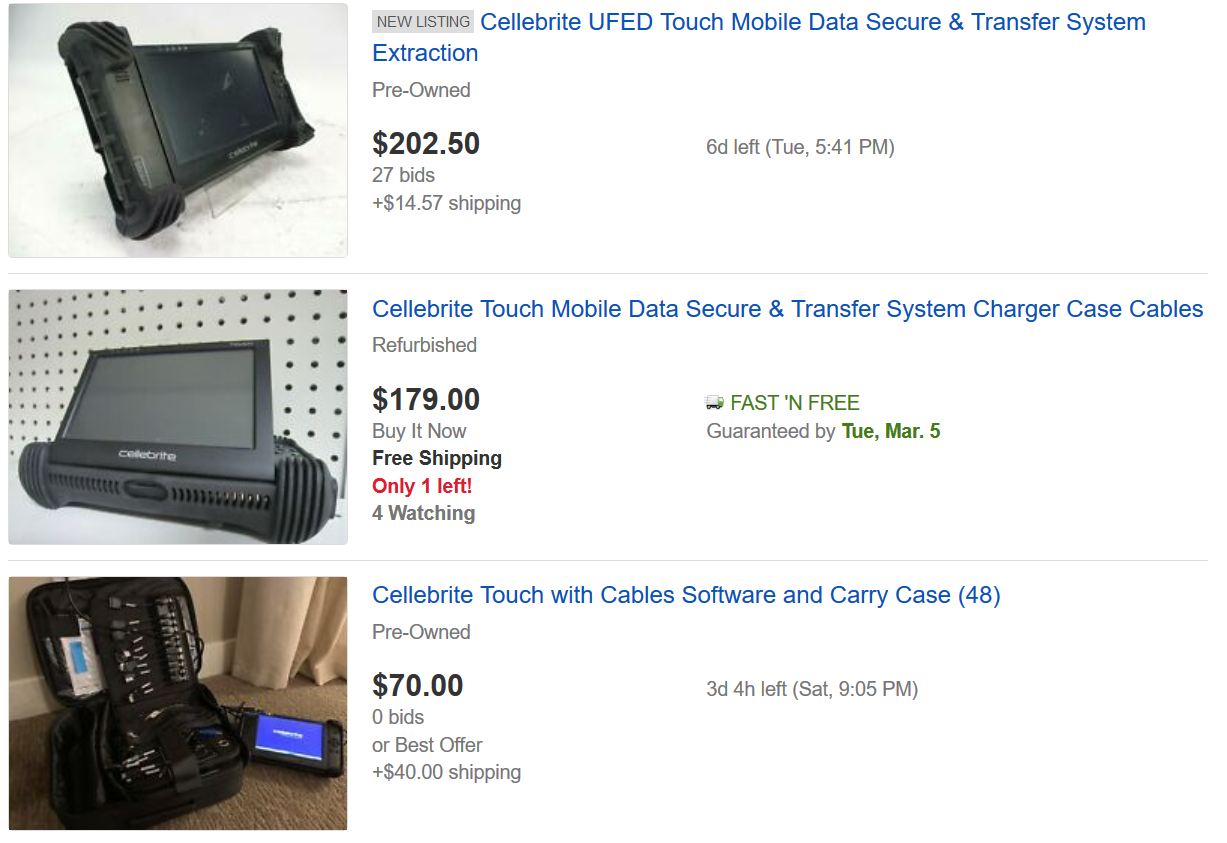
Examples of Cellebrite boxes and gear offered on eBay
Follow us on Google News













Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: