Unremovable Android malware will reinstall itself even after a factory reset

Imagine your worst malware nightmare, because it might be here now. ZDNet is reporting about a particular "strain" of malware that has the ability to reinstall itself making it nearly impossible for Android users to get rid of. Known as xHelper, the malware was first spotted in March and five months later it had infected 32,000 phones. That number hit 45,000 this month. According to Symantec, 131 new handsets are infected each day, approximately 2,400 each month.
The malware shows popup ads and notification spam that brings in revenue to those behind it. It also takes infected phones to the Google Play Store. There, phone owners are told to install premium websites which pay commissions to the bad actors. The malware can be loaded onto an Android phone through the use of redirects that send users to a website hosting Android apps. Some of these apps that users sideload on their Android phone contain the xHelper trojan.
Once one of the infected apps is installed, xHelper installs as a separate download and removing the original app it was attached to will not get rid of it. In fact, Android users will never get rid of xHelper as it will reinstall even after a factory reset! This remains a mystery to both software developers Symantec and Malwarebytes. Both say that xHelper doesn't mess with the Android OS or system apps. And some victims found that even after removing xHelper and disabling the "Install apps from unknown sources" option, the malware comes right back on the user's phone.
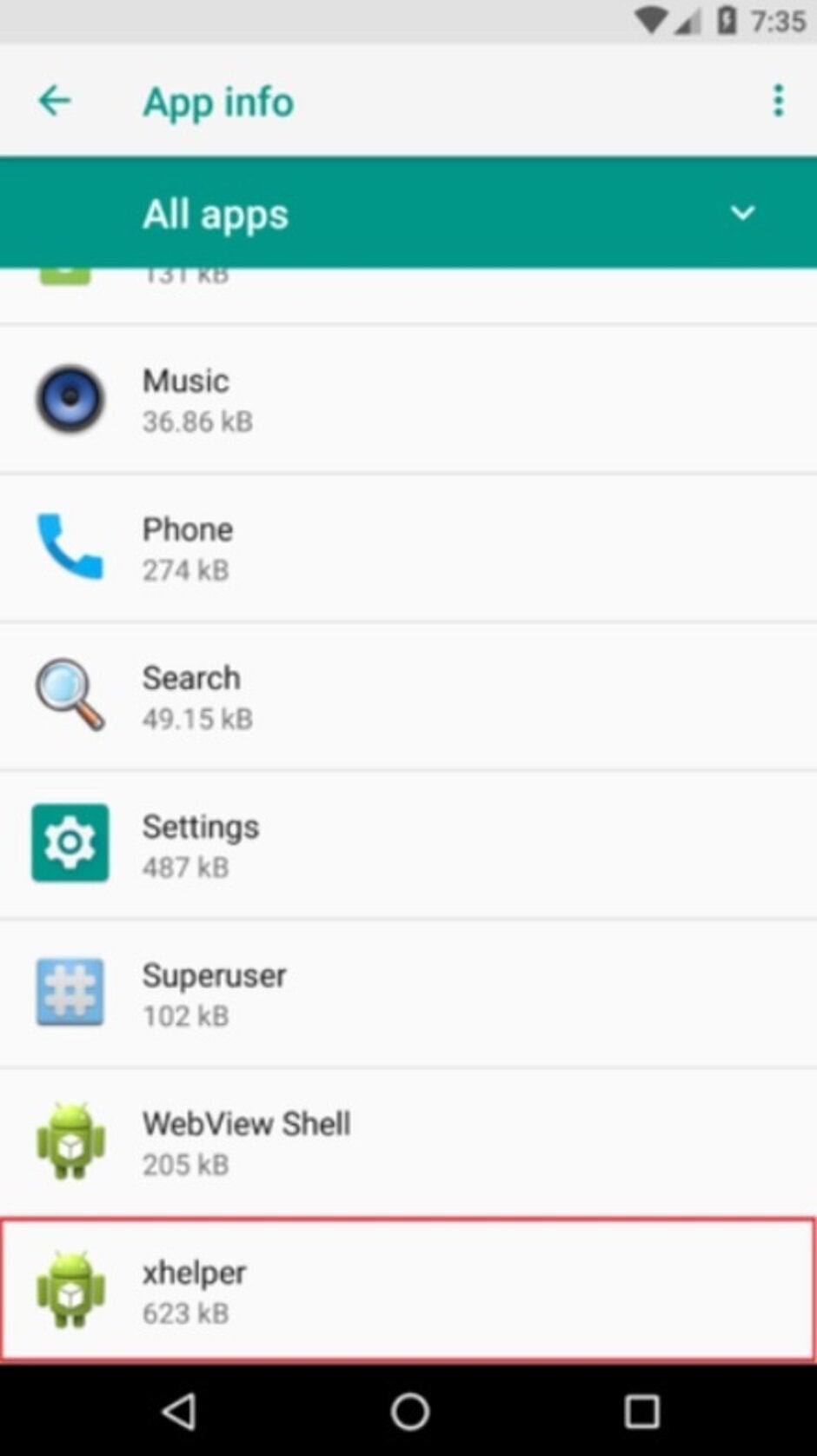
Android users just can't seem to get rid of xHelper
While some paid versions of mobile anti-virus software are said to work, there seems to be a battle between those responsible for the trojan and developers of the anti-virus software with each trying to get the better of the other. The scary part of xHelper is that there might be another shoe to drop. Those responsible for it could arrange for the trojan to release a payload that might include malware that will steal your banking information, passwords and other personal information.
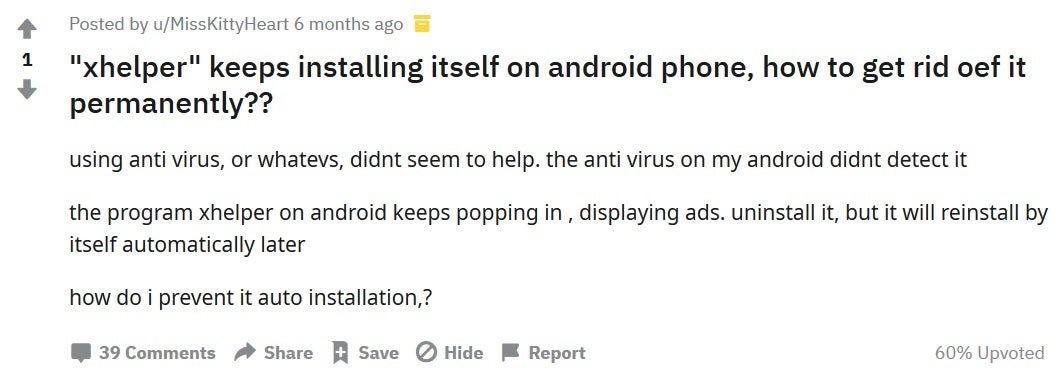
A warning from a Reddit user
A word to the wise: with xHelper possibly attached to any app you sideload, you might want to refrain from this practice except for those sideloads that come from a developer you know and absolutely trust.
Follow us on Google News












Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: