Here's why Apple iPhone users need to install Signal even if they don't use it

It has recently been revealed that Israeli company Cellebrite had nothing to do with the unlocking of the Apple iPhone 5c belonging to alleged San Bernardino shooter Syed Farook back in 2016. That honor and the $900,000 payday reportedly went to a little known firm named Azimuth, now a part of L3Harris Technologies. But that hasn't stopped Cellebrite from continuing to crack open iPhones on behalf of law enforcement.
Signal discovers vulnerabilities forcing Cellebrite to stop unlocking iPhone models with its Physical Analyzer
However, something has stopped Cellebrite dead in its tracks forcing it to stop using its top-of-the-line machine to open iPhone models. Cellebrite's Physical Analyzer has been called "the industry standard for digital data examination," but it can no longer be used to collect data from Apple's iOS powered smartphones. That's because messaging app Signal, as detailed in its blog (via 9to5Mac) discovered several vulnerabilities in Cellebrite software which corrupted scans of the iPhone.
- The new iPhone 13: price, release date, features, and specs
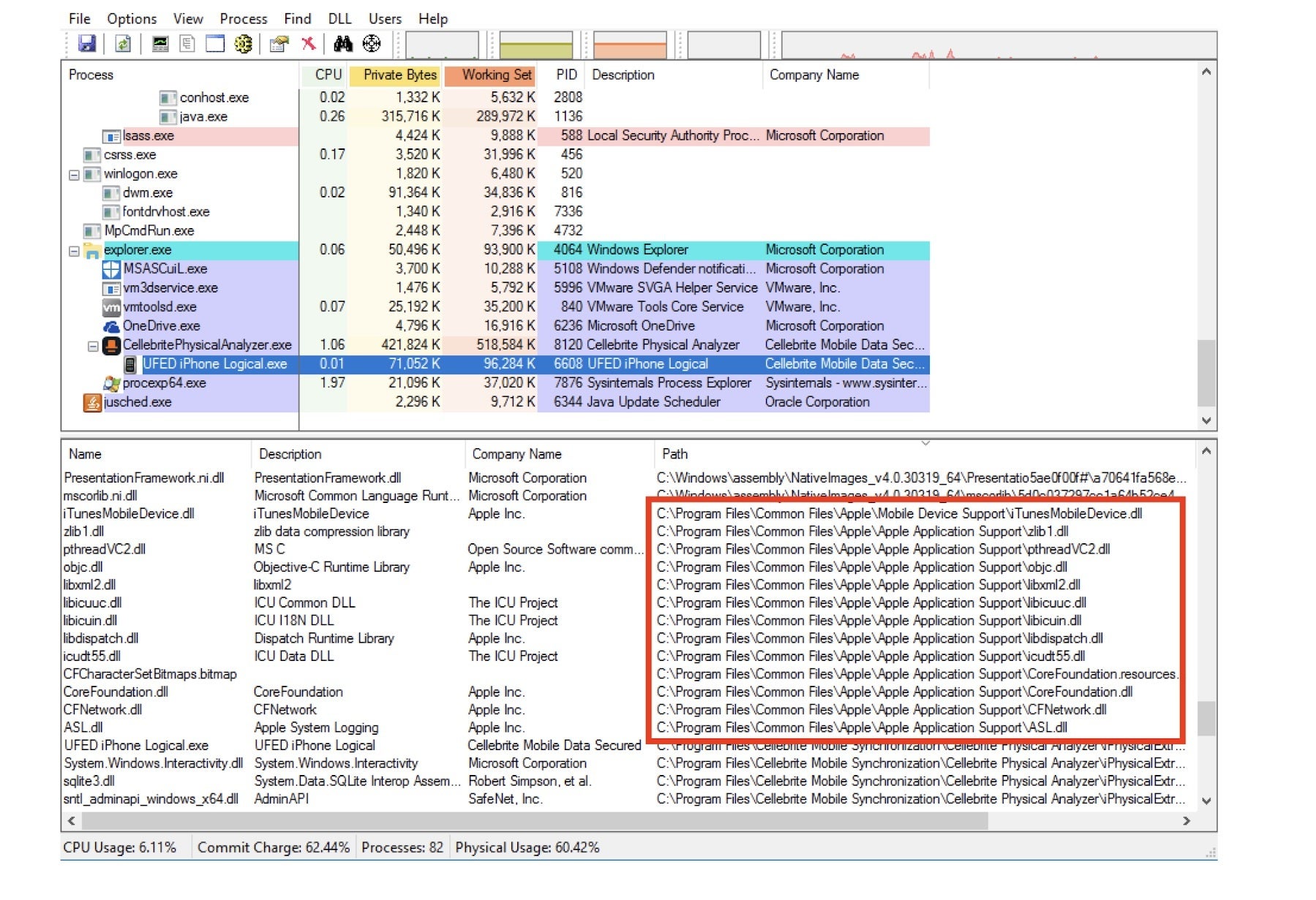
Apple DLL files that Signal says were used without permission to allow Cellebrite to extract data from iOS devices
These vulnerabilities, if exploited, would not only call into question the results of a current scan, but also past and future scans done with the same machine. It would be a prosecutor's nightmare and a dream come true-with extra whipped cream on top-for defense attorneys. And all Signal had to do was to place a file into the Cellebrite machine.
With Signal installing the file for all of its users, this has proven to be an incentive for iPhone users to install the messaging app even if they never use it. In its aforementioned blog, Signal explained the process of kicking Cellebrite where it hurts. This is done "by including a specially formatted but otherwise innocuous file in an app on a device that is then scanned by Cellebrite, it’s possible to execute code that modifies not just the Cellebrite report being created in that scan, but also all previous and future generated Cellebrite reports from all previously scanned devices and all future scanned devices in any arbitrary way (inserting or removing text, email, photos, contacts, files, or any other data), with no detectable timestamp changes or checksum failures. This could even be done at random, and would seriously call the data integrity of Cellebrite’s reports into question.
The ease with which Signal can do this is apparent from its comment that states "Any app could contain such a file, and until Cellebrite is able to accurately repair all vulnerabilities in its software with extremely high confidence, the only remedy a Cellebrite user has is to not scan devices. Cellebrite could reduce the risk to their users by updating their software to stop scanning apps it considers high risk for these types of data integrity problems, but even that is no guarantee."
Cellebrite's Physical Analyzer cannot be used right now to extract iOS data
One interesting discovery by Signal revealed that Cellebrite was using Apple DLL files to help it extract data from iOS devices. As Signal says in its blog, it is "unlikely" that Apple would give Cellebrite permission to use these files. The messaging app says that this use of Apple's files without permission "might present a legal risk for Cellebrite and its users."
Explaining how the DLL files are used, Signal notes, "The Cellebrite iOS Advanced Logical tool loads these Apple DLLs and uses their functionality to extract data from iOS mobile devices. The screenshot below shows that the Apple DLLs are loaded in the UFED iPhone Logical.exe process, which is the process name of the iOS Advanced Logical tool."
Signal was able to find the vulnerability by getting its hands on Cellebrite's software, including the the powerful Physical Analyzer. Signal found the vulnerabilities it discusses in its blog.
Signal said that it would be willing to "responsibly disclose the specific vulnerabilities we know about to Cellebrite." In return, Signal wants Cellebrite to do reveal all of the vulnerabilities that it uses to physically extract data and provide all of its services now and in the future to its "respective vendors."
Follow us on Google News














Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: