Delete these five apps now from your Android phone before your bank account is threatened

Unlike malicious apps that are dripping with malware making it harder to get listed in the Google Play Store (but not impossible, unfortunately), malware droppers look and act like your garden-variety apps. But when these apps notify users that an update is ready, what is really being installed is malware running in the background scooping up your banking information and other personal data.
Banking Trojans act like legit apps until you tap on the Update button
In a new blog post, Amsterdam computer support company Threat Fabric warns Android users about a new banking Trojan designed to steal your login info, account number, and other financial information that might help the attackers steal your hard-earned cash. Like the Greek's Trojan Horse, which from all appearances was a gift to the city of Troy only to be filled with Greek soldiers inside, Trojan malware ambushes users by looking like a legitimate app.
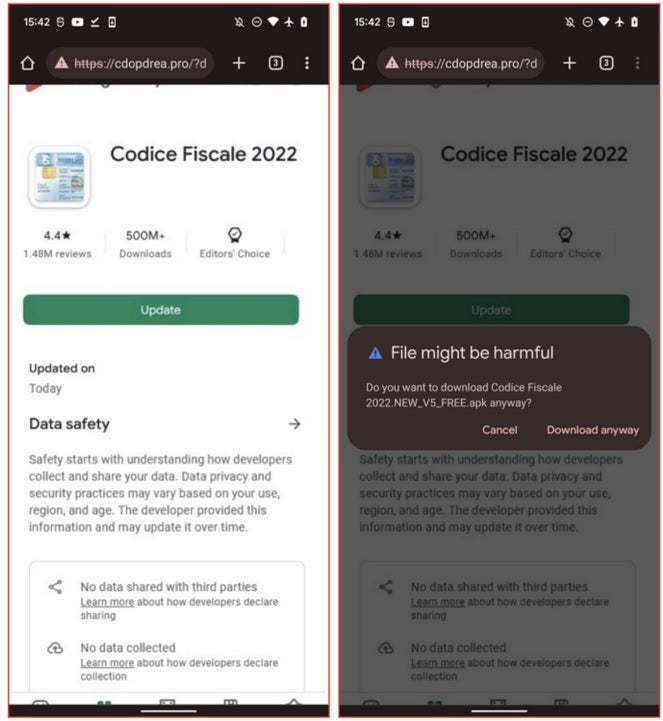
Fake Play Store listing asks you to update this malware dropper which actually installs a banking Trojan
Nonetheless, the report mentions that this new banking Trojan is called Sharkbot and one malware dropper purported to be an app to help users calculate their taxes in Italy. With over 10,000 installs, "Codice Fiscale" has an innocent-looking listing in the Play Store. If opened on a device, the app checks the country where the handset's SIM is registered. If it didn't match the code for Italy, no malicious behavior would take place.
If opened on a phone using a SIM registered in Italy, the app would open a fake Play Store page with a bogus listing for "Codice Fiscale." This fake listing also revealed that an update was available for the app, something that all users would probably tap on. And while some browsers might warn the user about the update, the owner of the phone could feel comforted by the fact that the app was installed from the Google Play Store and go ahead with the update.
What was really being loaded on the phone was the aforementioned banking Trojan. And if you think that you've escaped having your personal info from your banking app stolen because you don't live in Italy, you need to think again. Another dropper app, "File Manager Small, Lite," targets banking apps used in other countries such as the U.S., U.K., Austria and Australia, Italy, Germany, Spain, and Poland.
Another banking Trojan, this one called Vultur, has been disseminated by three malware droppers also found in the Play Store: "Recover Audio, Images & Videos," "Zetter Authentication" and "My Finances Tracker." The first app listed has over 100,000 installs. Vultur keeps track of all taps and gestures made by an Android user on his/her phone. Similar to Sharkbot, this ploy uses a fake update to load the malware on a handset.
Uninstall these five apps if they have been installed on your Android phone
To combat these malware droppers, normally we'd suggest checking the comments section for red flags. However, attackers have been known to load up the comments section with fake reviews. And after the initial installation of one of these apps, you might see a fake Google Play Store listing with phony reviews in an attempt to get you to tap the update button. The victim himself is inadvertently causing the malware to load on his own phone.
ThreatFabric says that it always reports malware droppers in an attempt to have them removed from app stores. But just because an app is removed from an app store doesn't mean it has been removed from your phone. So if you have one of these installed on your device, uninstall it immediately:
- Recover Audio, Images & Videos – 100,000 downloads
- Codice Fiscale 2022 - 10,000 downloads
- Zetter Authentication – 10,000 downloads
- File Manager Small, Lite - 1,000 downloads
- My Finances Tracker – 1,000 downloads
ThreatFabric adds, "Such way of distribution of Android banking Trojans is very dangerous as victims may stay unsuspecting for a long time and may not alert their bank about suspicious transactions made without them knowledge. Thus it is very important to take actions on the organization side to detect such malicious apps and their payloads as well as suspicious behavior happening on customer’s device."
Follow us on Google News










Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: