Latest Android security vulnerability exposes system data to rogue apps

Good smartphone security is all about vigilance; no matter what you do to make sure you've got the latest system updates installed, or keep all your apps up to date, it seems like there's always another threat right around the corner – and the first step towards protecting yourself from its fallout is knowing that threat exists. Today we learn about the latest vulnerability to impact Android devices, as a long-standing bug is finally uncovered.
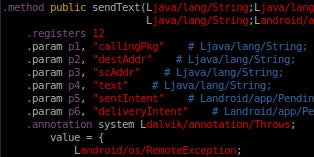
Potential risks include an app getting unauthorized access to call history, SMS logs, or being able to communicate over the internet without express permission to do so. We realize that none of these sound so severe as the consequences we saw with last year's Stagefright attacks, but with users for whom privacy is an especially salient concern, this vulnerability still has the potential to reveal sensitive personal data.
Our good news continues with word that Qualcomm's already developed a patch for the bug, and alerted its manufacturing partners back in March. But even that good news comes with an asterisk after it, as due to this bug being around for as long as it has, and migrating to Android forks like CyanogenMod, it's unlikely that many older devices will ever be patched, and even modern hardware running custom code may continue to be vulnerable.
source: FireEye via SlashGear
Follow us on Google News



![Some T-Mobile users might be paying more starting in March [UPDATED]](https://m-cdn.phonearena.com/images/article/176781-wide-two_350/Some-T-Mobile-users-might-be-paying-more-starting-in-March-UPDATED.webp)









Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: