Here's how Apple iPhone users can stop AirDrop from leaking personal data to hackers

AirDrop is a feature that allows Apple device users to send and receive photos, documents, and other files to a nearby iPhone or other compatible Apple devices without using cellular or Wi-Fi connectivity. The feature requires that both parties have Bluetooth and Wi-Fi turned on. That's because AirDrop relies on Bluetooth Low Energy (Bluetooth LE) to broadcast and find nearby connections, and while a Wi-Fi network is not required for AirDrop to work, files are transferred via point-to-point Wi-Fi.
AirDrop exploit can be used to steal your phone number and email address
Back in 2018, some iPhone users were experiencing a phenomenon known as cyber-flashing in which sexually explicit photos were randomly sent from an iPhone user in close quarters (such as a subway or airplane) to an unsuspecting iPhone user who does have the ability to decline the receipt of an AirDrop. But an image large enough to offend the random target is received even before the victim has the opportunity to decline the AirDrop.
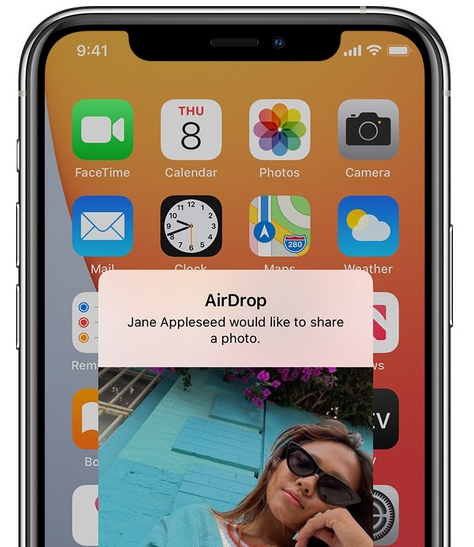
An AirDrop vulnerability allows hackers to steal a user's phone number and email address
As we told you at the time, the best way to prevent this was to change your settings to make your phone discoverable to "Contacts only" from "Everyone." Unless you have some pervs in your contacts list, this move should save you from receiving unwanted sexual images via AirDrop. And no, cyber-flashing is not what Apple designed Air Drop for.;
AirDrop is in the news again today after researchers at Germany's Technische Universitat Darmstadt have discovered what it calls a "severe privacy leak" that could pass along an iPhone user's phone number and email address to strangers without permission. All that a hacker would need is a device that can connect to Wi-Fi and is in close proximity to an Apple device with an open share sheet.
As the German research firm wrote in their blog (via AppleInsider), "As sensitive data is typically exclusively shared with people who users already know, AirDrop only shows receiver devices from address book contacts by default. To determine whether the other party is a contact, AirDrop uses a mutual authentication mechanism that compares a user's phone number and email address with entries in the other user's address book." While this data is encrypted by Apple, the researchers say that the method of hashing used by the tech giant can be reversed by using "brute-force attacks."
While the researchers developed a solution called "PrivateDrop" that replaces the use of hashed data with a more secure encryption technique, users can avoid giving up their phone number and email address by setting AirDrop to "Receiving off" on their device while keeping the share sheet closed. There are over 1.5 billion Apple devices that can be hit with this attack and the researchers informed Apple about the vulnerability in May 2019. Thus far, Apple has failed to acknowledge the problem and it has yet to state that it is working on a solution.
A scientific paper about this exploit was written by the researchers and will be presented by them at the USENIX security symposium in August. Perhaps by then Apple will feel the pressure to shine some light on this issue and start working on a solution that will fix the problem. AirDrop is available on certain Apple devices including iPhone 5 or newer, 4th generation iPad or newer, all iPad Air, iPad Pro, iPad mini models, fifth generation iPod touch and newer, with all running iOS 7 or later.
It also is available on certain Macs running Mac OS X 10.7 and later (via the Finder sidebar). On Macs powered by OS X 10.8.1 or later use the menu option Go → AirDrop or tap on Shift + Command + R).
Apple introduced its new MagSafe line of accessories with the unveiling of the iPhone 12 series. We've picked out the best ones for you and can find out which accessories they are by clicking on the link.







Things that are NOT allowed: