Good smartphone security is
all about vigilance; no matter what you do to make sure you've got the latest system updates installed, or keep all your apps up to date, it seems like there's always another threat right around the corner – and the first step towards protecting yourself from its fallout is knowing that threat exists. Today we learn about the latest vulnerability to impact Android devices, as a long-standing bug is finally uncovered.
The vulnerability in question appears to have been introduced sometime around 2011, and is known to affect devices running releases as recent as Lollipop. The exploit is of the privilege escalation variety, letting malicious apps achieve greater access to system resources than the user may be aware of.
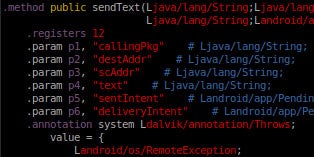
Basically, a flaw in a Qualcomm-designed Android API related to tethering and network management allows apps to overstep their own permissions and execute tasks as the system's “radio” user – one with plenty of access to network and call data.
Potential risks include an app getting unauthorized access to call history, SMS logs, or being able to communicate over the internet without express permission to do so. We realize that none of these sound so severe as the
consequences we saw with last year's Stagefright attacks, but with users for whom privacy is an especially salient concern, this vulnerability still has the potential to reveal sensitive personal data.
The good news is that while this issue is still present in modern devices, it tends to be less useful to malicious apps in more recent Android versions. That said, the researchers who discovered the bug suggest that OEM changes to system code could cause the full impact of the flaw to vary between devices otherwise on the same Android version, so it's difficult to make blanket statements about possible risk.
Our good news continues with word that Qualcomm's already developed a patch for the bug, and alerted its manufacturing partners back in March. But even that good news comes with an asterisk after it, as due to this bug being around for as long as it has, and migrating to Android forks like CyanogenMod, it's unlikely that many older devices will ever be patched, and even modern hardware running custom code may continue to be vulnerable.
source:
FireEye via
SlashGear













Things that are NOT allowed: